-
- What Is Extended Detection and Response (XDR)?
- What Is Security Information and Event Management (SIEM)?
- Key Differences Between XDR and SIEM
- Benefits and Limitations of XDR
- Benefits and Limitations of SIEM
- How to Choose the Right Solution for Your Organizational Needs
- Future Trends and the Evolution of XDR and SIEM
- XDR vs. SIEM FAQs
What is the Difference Between XDR vs. SIEM?
5 min. read
Table of Contents
XDR (extended detection and response) and SIEM (security information and event management) are both cybersecurity solutions, but they differ in their approach and scope.
The key difference between XDR and SIEM is the scope and integration of security data. SIEM primarily focuses on log data from various sources within the network, whereas XDR encompasses a broader range of security telemetry data, including endpoint data, network traffic, and cloud-based environments. XDR provides a more unified view of the organization's security posture and enables cross-layer threat detection and response. It goes beyond the capabilities of traditional SIEM solutions by leveraging advanced analytics and automation to detect and respond to threats across the entire IT environment.

Figure 1: Source: Forrester blogs, XDR FAQ — Frequently Asked Questions On Extended Detection And Response, July 2021.
What Is Extended Detection and Response (XDR)?
Extended detection and response (XDR) is a comprehensive cybersecurity solution that combines multiple security technologies and data sources to provide enhanced threat detection, response, and remediation capabilities. XDR expands beyond traditional endpoint detection and response (EDR) solutions and incorporates additional security telemetry data from various sources, such as network traffic, cloud environments, and other endpoints.
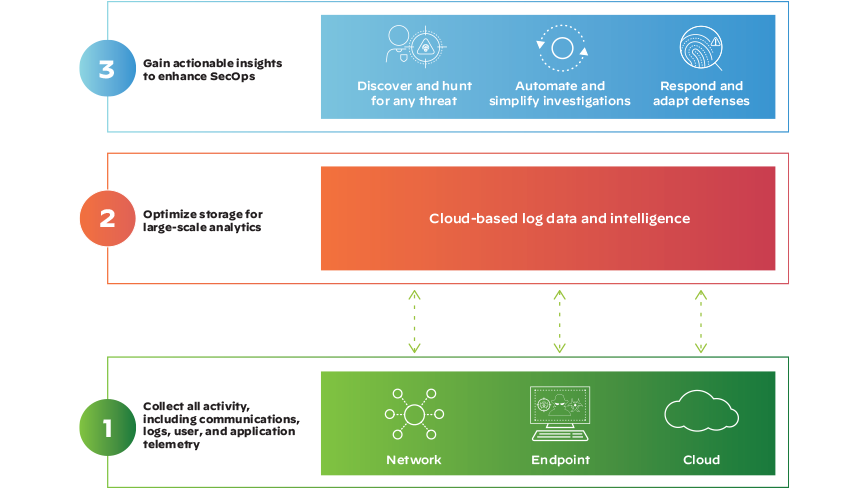
Figure 2: XDR breaks the traditional silos of detection and response.
Purpose and Capabilities of XDR
The core objective of XDR is to provide a unified and holistic view of an organization's security landscape, enabling security teams to detect, investigate, and respond to sophisticated threats more effectively. By collecting and correlating security data from multiple sources, XDR enables cross-layer threat detection and response, uncovering hidden threats that may not be visible when analyzing individual security silos.
Key features and benefits of XDR include:
- Enhanced visibility: XDR collects and analyzes data from diverse sources, including endpoints, network traffic, cloud platforms, and more. This broader visibility provides a comprehensive understanding of the organization's security posture and allows for the detection of complex threats that may span multiple layers.
- Advanced analytics and detection: XDR leverages advanced analytics, machine learning, and threat intelligence to detect and prioritize potential security incidents accurately. By applying behavioral analytics and anomaly detection, XDR can identify and flag suspicious activities or indicators of compromise.
- Automated and streamlined response: XDR streamlines the incident response process by automating investigation and remediation actions. It can orchestrate response activities across different security tools and endpoints, reducing the time and effort required to contain and mitigate threats.
- Threat hunting capabilities: XDR enables proactive threat hunting by allowing security teams to search for indicators of compromise (IoCs) and suspicious activities across the entire security ecosystem. This helps in identifying and eliminating threats before they cause significant damage.
- Improved operational efficiency: By consolidating and correlating security data from multiple sources, XDR simplifies security operations and reduces alert fatigue. It provides context-rich insights and actionable intelligence, enabling security teams to focus on critical threats and respond more efficiently.
What Is Security Information and Event Management (SIEM)?
Security information and event management (SIEM) is a cybersecurity solution that helps organizations collect, analyze, and correlate security event data from various sources within their IT infrastructure. SIEM systems provide real-time monitoring, threat detection, incident response, and compliance management capabilities.
Purpose and Capabilities of SIEM
The following are the key components and functions of SIEM.
Data Collection
SIEM collects log data, security events, and system activity logs from a wide range of sources, including network devices, servers, applications, firewalls, intrusion detection systems (IDS), and more. These logs contain valuable information about security events, user activities, and system behavior.
Log Management
SIEM systems store and manage log data in a centralized repository or database. This allows for easy search, retrieval, and long-term retention of logs for compliance and forensic purposes.
Event Correlation
SIEM analyzes and correlates log data from different sources to identify patterns, anomalies, and potential security incidents. It applies predefined rules or algorithms to match events and generate meaningful alerts or notifications.
Real-Time Monitoring
SIEM continuously monitors security events in real time and provides dashboards and visualizations to give security teams a holistic view of the organization's security posture. It allows them to track activities, detect threats, and respond promptly to incidents.
Threat Detection
SIEM uses rule-based correlation or advanced analytics techniques to detect potential security threats and malicious activities. It can identify patterns that indicate attacks, such as brute-force login attempts, suspicious network traffic, or unauthorized access attempts.
Incident Response
SIEM provides workflows and automation capabilities to streamline incident response processes. It enables security teams to investigate and respond to security incidents efficiently, including threat containment, analysis, and remediation.
Compliance Management
SIEM assists organizations in meeting regulatory compliance requirements by collecting and analyzing security logs for auditing purposes. It generates reports and provides evidence of compliance with standards such as PCI DSS, HIPAA, GDPR, and others.
Log Retention and Forensics
SIEM systems store logs for extended periods, allowing security teams to perform forensic analysis and investigations when necessary. This helps in understanding the scope and impact of security incidents and supports post incident remediation efforts.
Key Differences Between XDR and SIEM
When comparing XDR (extended detection and response) and SIEM (security information and event management) in terms of scope and coverage, there are several key differences:
1. Data Sources:
- SIEM primarily focuses on log data from various sources within the network, such as firewalls, servers, applications, and network devices. It collects and analyzes logs to identify security events and generate alerts.
- XDR goes beyond logs and incorporates a broader range of security telemetry data. It collects and analyzes data from diverse sources, including endpoints, network traffic, cloud environments, and sometimes additional sources like cloud applications, email gateways, or user behavior analytics.
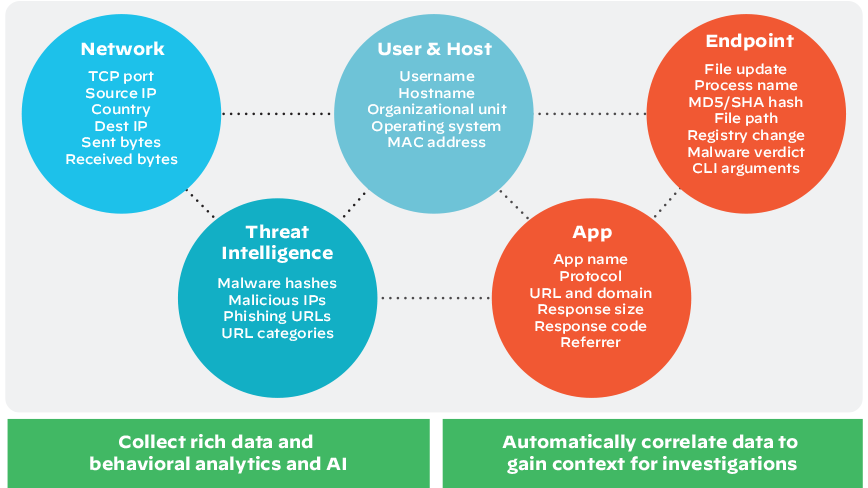
Figure 3: XDR collects data from any source, correlating and stitching it together for better detection and hunting.
2. Endpoint vs. Network Focus:
- SIEM traditionally places more emphasis on network-focused data sources, analyzing logs from network devices and servers. While it can incorporate some endpoint data, the primary focus is on network-centric security events.
- XDR expands the scope to include both endpoint and network data. It incorporates endpoint detection and response (EDR) capabilities, analyzing endpoint activities, processes, and behaviors. It also includes network detection and response (NDR) functionalities to monitor network traffic and identify threats.
3. Threat Detection Approach:
- SIEM typically relies on rule-based correlation and signature-based detection to identify security incidents. It uses predefined rules and signatures to match events and generate alerts based on known patterns.
- XDR leverages advanced analytics, machine learning, and threat intelligence to detect sophisticated threats. It applies behavioral analytics, anomaly detection, and machine learning algorithms to identify anomalies, unknown threats, and indicators of compromise.
4. Response and Automation:
- SIEM systems provide alerting and reporting capabilities, allowing security teams to investigate and respond to incidents manually. While some level of automation is possible, the focus is primarily on generating alerts and providing analysis for human decision-making.
- XDR offers more extensive automation and orchestration capabilities. It can automate response actions, such as isolating compromised endpoints, blocking malicious network traffic, or initiating remediation tasks.
5. Holistic View and Context:
- SIEM provides visibility into security events and logs, allowing security teams to monitor activities and detect threats within the network.
- XDR aims to provide a unified and holistic view of the organization's security posture. By collecting and correlating data from various sources, including endpoints, network, and cloud,
Benefits and Limitations of XDR
XDR (extended detection and response) offers several benefits as a comprehensive cybersecurity solution, but it also has certain limitations. Let's explore them:
Benefits of XDR
Enhanced Threat Detection: XDR expands the scope of threat detection beyond traditional endpoint-focused solutions. By collecting and correlating data from multiple sources such as endpoints, network traffic, and cloud environments, XDR provides better visibility and increases the chances of detecting sophisticated and multilayered threats.
Holistic Visibility and Context: XDR provides a unified view of an organization's security posture by aggregating and correlating data from various security telemetry sources. This broader visibility and contextual information enables security teams to gain a comprehensive understanding of security events and incidents, facilitating faster and more accurate response actions.
Cross-Layer Detection and Response: XDR enables the correlation of data across different security layers, such as endpoints and networks. This cross-layer analysis helps in identifying advanced threats that may manifest differently across multiple components of the IT infrastructure. It allows for a more effective response by addressing the entire attack chain.
Advanced Analytics and Threat Intelligence: XDR leverages advanced analytics techniques and threat intelligence to identify and prioritize potential threats accurately. Behavioral analytics, machine learning, and anomaly detection algorithms enable XDR to detect unknown threats, zero-day exploits, and suspicious activities that may go unnoticed by rule-based systems.
Automated Response and Orchestration: XDR offers automation capabilities for incident response. It can automate response actions, such as isolating compromised endpoints, blocking malicious network traffic, or initiating remediation tasks. This automation reduces manual effort and speeds up the response time to mitigate threats.
Limitations of XDR
Complexity and Deployment Challenges: Implementing XDR can be complex, especially in larger organizations with diverse IT environments. Integrating multiple security technologies, configuring data collection, and ensuring compatibility across various systems can be challenging and require skilled personnel.
Data Collection and Privacy Considerations: XDR relies on collecting data from multiple sources, including endpoints, networks, and cloud platforms. Organizations must ensure proper data collection practices and address privacy concerns to meet regulatory requirements and maintain customer trust.
Cost and Resource Requirements: XDR solutions often come with a higher price tag compared to standalone security solutions like SIEM or EDR. They require investment in hardware, software, licenses, and ongoing maintenance. Additionally, organizations need skilled personnel to manage and operate the XDR platform effectively.
False Positives and Alert Fatigue: Due to the complex and diverse data sources involved, XDR may generate a significant number of alerts. Managing and prioritizing these alerts can be challenging, and false positives may occur, leading to alert fatigue and potentially diverting resources from critical threats.
Integration Challenges: Integrating XDR with existing security infrastructure, including SIEM or other security tools, may require additional configuration and customization efforts. Ensuring seamless integration and interoperability can be complex, requiring careful planning and expertise.
Benefits and Limitations of SIEM
Benefits of SIEM
Centralized Log Management: SIEM systems collect and consolidate log data from various sources within an organization's IT infrastructure. This centralized log management allows for efficient storage, retrieval, and analysis of security event data, aiding in compliance audits, forensic investigations, and troubleshooting.
Real-Time Threat Monitoring: SIEM provides real-time monitoring of security events and activities across the network. It analyzes log data and applies correlation rules to identify suspicious activities, potential security incidents, or policy violations. This enables prompt detection and response to mitigate threats.
Compliance Management: SIEM solutions help organizations meet regulatory compliance requirements by collecting and analyzing security event logs. They generate reports and provide evidence of adherence to industry standards such as PCI DSS, HIPAA, GDPR, and others. SIEM aids in demonstrating compliance during audits and regulatory inspections.
Customization: SIEM affords security organizations the ability to create very customized threat detection content (e.g., rules) and, in some cases, data analytics. Most SIEM solutions allow the user to create personalized dashboards based on persona or individual need. SIEM often provides more complex query and rule creation languages and interfaces for advanced users.
Limitations of SIEM
Rule-based detection: SIEM systems primarily rely on rule-based correlation to detect security incidents. These rules need to be continuously updated and fine-tuned to adapt to new threats and changing environments. SIEM may struggle to detect advanced or unknown threats that do not match predefined rules.
False positives and alert overload: SIEM solutions can generate a large number of alerts, including false positives. Managing and prioritizing these alerts can be challenging and time-consuming, potentially leading to alert fatigue and diverting resources from critical threats.
Limited endpoint visibility: SIEM's focus is primarily on network-centric log data, which may provide limited visibility into endpoint activities. While some SIEM solutions integrate with Endpoint Detection and Response (EDR) tools, achieving comprehensive endpoint visibility and analysis may require additional efforts and integration.
Deployment complexity: Implementing SIEM can be complex and resource-intensive, especially for large-scale deployments. It involves configuring log sources, defining correlation rules, and integrating with existing security infrastructure. Organizations need to allocate sufficient resources and expertise to effectively deploy and maintain the SIEM solution.
High initial and ongoing costs: SIEM solutions often come with significant upfront costs, including hardware, software licenses, and implementation expenses. Ongoing costs may include maintenance, updates, and dedicated personnel for managing and optimizing the SIEM platform.
How to Choose the Right Solution for Your Organizational Needs
Choosing between XDR (extended detection and response) and SIEM (security information and event management) depends on your organization's specific needs and requirements. Here are some factors to consider when making a decision:
Scope and Coverage
If you primarily need log management, real-time event monitoring, and compliance management, SIEM may be a suitable choice. However, if you require broader visibility, including endpoint and network telemetry data, and the ability to detect and respond to advanced threats, XDR offers a more comprehensive solution.
Threat Detection and Response Capabilities
SIEM focuses on log-based correlation and rule-based detection, while XDR leverages advanced analytics, machine learning, and behavioral analytics for more proactive and adaptive threat detection. If you need advanced threat detection capabilities and automated response actions, XDR may be a better fit.
Integration and Existing Infrastructure
SIEM solutions often integrate well with other security tools and systems, allowing for seamless integration and leveraging existing investments. If you have a well-established security stack and want to enhance log management and correlation capabilities, SIEM may be the preferred choice. On the other hand, if you require integration with endpoint security tools, network monitoring solutions, and cloud platforms, XDR offers a more holistic approach.
Resource Availability and Skill Set
Implementing and managing SIEM or XDR solutions may require dedicated personnel with specific skills. SIEM solutions often require expertise in log management, correlation rule creation, and compliance auditing. XDR solutions may involve managing endpoint agents, network sensors, and advanced analytics tools. Assess whether you have the necessary resources and skill sets in-house or if you need to consider external assistance or managed services.
Budget Considerations
SIEM solutions typically have varying cost structures, including upfront costs, licensing fees, and ongoing maintenance expenses. XDR solutions may involve additional costs, such as endpoint agents, network sensors, and analytics tools. Consider your budget and weigh the benefits and value provided by each solution to determine the most cost-effective option for your organization.
Regulatory and Compliance Requirements:
SIEM solutions often offer compliance management features and reporting capabilities, aiding in regulatory audits. If compliance is a primary concern, SIEM may be a suitable choice. However, XDR solutions also provide valuable telemetry data and incident response capabilities that contribute to meeting compliance requirements.
Future Trends and the Evolution of XDR and SIEM
Both XDR (extended detection and response) and SIEM (security information and event management) are evolving to address emerging cybersecurity challenges and keep pace with advancements in technology. Here are some future trends and potential evolutions for XDR and SIEM:
Evolution of XDR
XDR is expected to gain broader adoption as organizations recognize the benefits of a unified, holistic approach to threat detection and response. The growing complexity of cyberthreats and the need for comprehensive visibility across endpoints, networks, and cloud environments will drive the adoption of XDR solutions.
With the increasing migration of workloads and applications to the cloud, XDR solutions will evolve to be more cloud-native. This means they will be specifically designed to collect and analyze data from cloud platforms and applications, ensuring comprehensive coverage and detection capabilities in cloud environments.
XDR solutions may integrate more closely with identity and access management (IAM) systems to enhance user behavior analytics and identify anomalous activities related to user accounts and access privileges. This integration will provide better insights into insider threats and help organizations strengthen their security posture.
Automation and orchestration capabilities will continue to improve in XDR solutions. This includes automated response actions, remediation tasks, and playbooks for incident response. XDR platforms will leverage AI and machine learning algorithms to automate routine security operations and enable faster response to threats.
Evolution of SIEM
SIEM solutions will increasingly leverage advanced analytics techniques, such as machine learning and artificial intelligence, to improve threat detection and reduce false positives. These technologies will enhance the ability of SIEM platforms to identify complex attack patterns and zero-day threats.
Cloud adoption is driving the emergence of cloud-based SIEM solutions. Cloud-based SIEM offerings provide scalability, flexibility, and reduced maintenance overhead. They enable organizations to benefit from the advantages of cloud infrastructure while maintaining robust security monitoring and compliance management.
SIEM platforms will integrate more tightly with security orchestration, automation, and response (SOAR) tools. This integration will enable seamless coordination between threat detection, incident response, and automated remediation actions, streamlining security operations and reducing response times.
SIEM solutions will further enhance their capabilities in user behavior analytics. By analyzing user activities, access patterns, and behaviors, SIEM platforms will help organizations detect insider threats, account compromise, and anomalous user behavior, improving overall security posture.
SIEM solutions will play a crucial role in facilitating threat intelligence sharing among organizations. Increased collaboration and information sharing between security teams and across industries will strengthen collective defenses against cyberthreats and enable faster threat detection and response.
XDR (extended detection and response) provides a comprehensive, integrated approach to threat detection and response by correlating data from extended detection and response curves. SIEM (security information and event management) focuses on log management, real-time event monitoring, and compliance management.
XDR is typically considered better for advanced threat detection. It leverages advanced analytics, machine learning, and behavioral analytics to detect unknown threats, zero-day exploits, and suspicious activities that may go unnoticed by rule-based SIEM systems.
Yes, SIEM solutions often offer dedicated compliance management features, such as generating compliance reports and facilitating regulatory audits. XDR solutions, while providing valuable telemetry data, may not have the same level of compliance-focused functionality.
Yes, XDR and SIEM can be used together to complement each other's capabilities. Organizations may choose to integrate their SIEM solution with an XDR platform to enhance their threat detection and response capabilities, leveraging the strengths of both solutions.
SIEM solutions typically require significant resources and expertise for implementation and ongoing management. They involve configuring log sources, defining correlation rules, and integrating with existing security infrastructure. XDR solutions may also require skilled personnel to manage and operate the platform effectively, particularly with endpoint agents, network sensors, and advanced analytics tools.