What Is Network Detection and Response (NDR)?
Network Detection and Response (NDR) technology emerged in the early 2010s to identify and stop evasive network threats that couldn't be easily blocked using known attack patterns or signatures. NDR, also referred to as network traffic analysis (NTA), technology uses machine learning and behavioral analytics to monitor network traffic and develop a baseline of activity. Then they discover anomalous activity associated with malware, targeted attacks, insider abuse, and risky behavior.
NDR solutions allow organizations to recognize unusual traffic that indicate command and control, lateral movement, exfiltration, and malware activity. They analyze north-south traffic between internal hosts and the internet, but they also inspect east-west traffic between internal hosts, including internal servers, to accurately identify attacks.
According to the 2020 Gartner Market Guide for Network Detection and Response, NDR solutions “primarily use non-signature-based techniques (for example, machine learning or other analytical techniques) to detect suspicious traffic on enterprise networks. NDR tools continuously analyze raw traffic and/or flow records (for example, NetFlow) to build models that reflect normal network behavior. When the NDR tools detect suspicious traffic patterns, they raise alerts... Response is also an important function of NDR solutions."
Unlike many log management and security analytics products that focus on security alerts, NDR solutions analyze raw network traffic logs to identify threats. While they can also be deployed as a passive network element that collects data from network switch SPAN ports or physical TAPs, an increasing number of NDR solutions today can gather network traffic data from existing network infrastructure, such as network firewalls, easing deployment.
What Types of Threats Do Network Detection and Response Solutions Uncover?
The four main types of cybersecurity risks identified by NDR solutions include:
- Unknown Malware: External attackers that leverage undetectable malware to compromise and control host(s) on your network
- Targeted Attacks: External attackers that leverage social engineering, exploits, brute force attacks or other techniques to compromise applications or endpoints, steal legitimate user credentials, establish command and control, move laterally and steal, manipulate or destroy data.
- Insider Attacks: Employees or contractors engaged in a range of behavior including accessing, stealing, manipulating files and data, changing access permissions, installing malware, and more.
- Risky Behavior: Well-meaning but reckless employees can expose organizations to attack. Risky behavior includes sharing user accounts, exposing sensitive data to unauthorized users, enabling remote access to endpoints, and more.
DID YOU KNOW? |
NDR solutions profile network behavior metadata, not payloads and files; thus, they can operate effectively regardless of encrypted or unencrypted communication protocols, like HTTPS. |
Five Benefits of Network Detection and Response
NDR solutions provide powerful attack detection capabilities for both internal and external attackers.
- Broad Attack Visibility to Avoid False Negatives
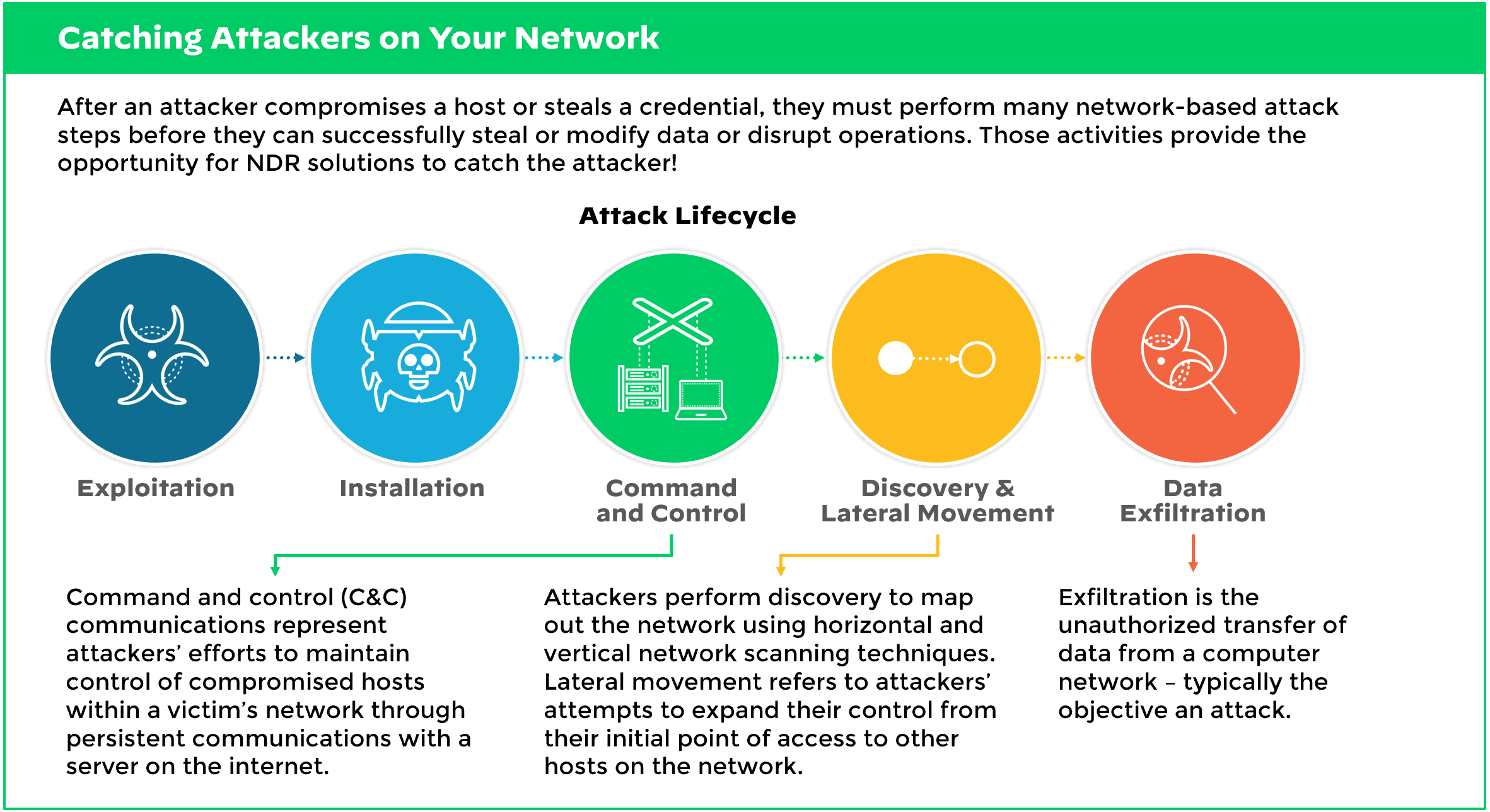
NDR solutions literally see every network event that an attacker performs. Unless the attacker directly gains access to the one host with targeted, valuable or sensitive data, the attacker must perform hundreds of network activities to achieve their ultimate objective. NDR solutions can see all these events, including the early network-based command and control and discovery activities that will rarely, if ever, create a log event. And, of course, NDR products also see the later stages of an attack, including lateral movement and exfiltration activities.
If organizations do not monitor network traffic, they will often miss discovery or internal recon activities, which is the most iterative and potentially lengthy portion of the active attack. They will rarely find network activities, including network scans, port scans, command and control communications, and other network-based attack tactics. - Early Detection to Mitigate Attacks Before the Damage Is Done
The earlier you can detect attacks, the earlier you can stop attackers in their tracks. The average attack dwell time has been well documented by many post-incident response surveys to average between five and seven months. If you can detect, investigate and stop an attacker in the early hours or days of the attack, then it’s likely that you can eliminate all potential damage. With visibility into the earliest stages of the attack, NDR solutions can identify those unusual network events related to command and control communications and discovery activities.
Unless security teams analyze network data for anomalies indicative of attacks, they will struggle to find attackers during the critically important early stages of the attack and, therefore, won't be able stop most attacks before real damage is done. - Avoid the Inefficiencies of Garbage In, Garbage Out Analytics
NDR platforms analyze raw network packets to learn user and device behavior and unearth attacks. They use advanced machine learning technology to profile the network behavior of all entities and detect the anomalous attack behaviors, instead of relying on third-party systems that can’t baseline activity over time or accurately uncover stealthy threats that blend in with legitimate activity. The network never lies. It represents every single activity and cannot be tampered with or deleted. The almighty packet is the best source of truth providing visibility into all network behavior. - Broad Analytical Data Inputs to Increase Accuracy
NDR solutions have broad context to see all network events that an attacker performs, which can improve the accuracy of attack detections. They can see all aspects of an attacker’s tactics and techniques: the network reconnaissance activities, the user credentials employed in lateral movement, the administrative behaviors, the rare file shares accessed, the command and control sites contacted, and potentially even the endpoint process responsible for the network event. By triangulating on the attacker from different attack perspectives, NDR products can therefore provide much higher confidence that an attack is occurring. This validation avoids the false positives that plagues many cybersecurity tools. For example, a user credential identified to be making anomalous access to a rarely accessed file share or internet domain can also be correlated to a host device performing rare port scanning behaviors or internet communications. By examining multiple dimensions of behavior and comparing current behavior to a baseline, they can increase detection accuracy. - Out-of-the-box detection without extensive tuning
NDR platforms do not require the configuration of logs or normalization of log formats or to extract behavior. Network packets are readily accessible and have all the actual content readily available for NDR systems to parse and store. And, a well-designed system can efficiently extract and store only the most relevant behavioral metadata needed to perform accurate behavioral profiling and attack detection. Thus, these out-of-the-box capabilities reduce operational overhead. - Zero network footprint with cloud-delivered analytics
Today’s network detection and response tools are delivered from the cloud. This cloud-native approach simplifies operations because teams do not need to deploy new log servers on premises to collect and analyze network data. In addition, advanced NDR platforms can collect network logs from existing network security products, including network firewalls, avoiding dedicated network sensors. Altogether, NDR systems offer full visibility and threat detection, with minimal overhead.
The Shortcomings of Network Detection and Response
Security teams that want to hunt down active attackers at the earliest possible stages of the attack life cycle should monitor network traffic for attacks. However, despite their benefits, NDR tools also have their limitations. They only analyze network logs and can’t monitor or track endpoint events, such as process details, registry changes or system commands. They cannot examine cloud or identity data or other valuable sources of security information. Complex attacks require analysis of multiple data sources to identify and confirm malicious activity. Siloed cybersecurity tools like NDR solutions are costly to deploy and maintain, create potential blind spots, and force security analysts to switch between consoles to gather context.
Join the XDR revolution
Traditional network detection and response tools focus on network data only. This narrow scope of analysis can result in missed detections, increased false positives and lengthy investigations. These weaknesses magnify the problems many security teams already face, including too many siloed tools, too many alerts and too little time.
Extended detection and response, or XDR, is a new approach to threat detection and response. XDR expands the scope of security beyond one data source, such as endpoint, network, cloud, or identity data, recognizing that it’s not effective to investigate incidents in isolated silos. XDR platforms automatically stitch together data from different sources and apply use artificial intelligence (AI) to uncover covert cyber threats. This increases visibility and productivity compared to siloed security tools. The result is simplified investigations across security operations, reducing the time it takes to identify, verify, and respond to attacks.
Stop Evasive Network Attacks with Cortex XDR
Cortex XDR detects targeted attacks, insider abuse and malware by applying AI-powered analytics to rich security data. Your analysts can rapidly confirm threats by reviewing actionable alerts with full context and quickly shut down attacks through tight integration with enforcement points.
Cortex XDR is the industry’s first extended detection and response platform that integrates data from virtually any source to stop sophisticated attacks. Cortex XDR has been designed from the ground up to protect your whole organization holistically while simplifying operations. It delivers best-in-class next-gen antivirus (NGAV) to stop exploits, malware, ransomware, and even non-malware attacks.
Cortex XDR uses behavioral analytics to reveal highly evasive threats targeting your network. Machine learning and AI models uncover threats from any source, including managed and unmanaged devices. Because Cortex XDR gathers data from network devices, including Palo Alto Networks NGFW, it can uncover hidden threats lurking in your network. It also gathers endpoint data from the Cortex XDR agent to deliver full endpoint detection and response (EDR).
Cortex XDR helps you speed investigations by providing a complete picture of each incident. It stitches different types of data together and reveals the root cause and timeline of alerts, allowing your analysts to easily triage alerts. Flexible response options let you root out attackers, contain fast-moving threats, and even restore compromised endpoints.
Network Detection and Response FAQs
Key features of an effective NDR solution include:
- Advanced Threat Detection: Utilizing machine learning and behavioral analytics to identify threats.
- Real-Time Response: Automated response capabilities to quickly mitigate detected threats.
- Comprehensive Network Visibility: Monitoring all network traffic, including encrypted traffic, to ensure no blind spots.
- Scalability: The ability to scale with the network's growth and adapt to changing threat landscapes.
- Integration: Seamless integration with existing security tools such as SIEM and EDR for a unified defense strategy.
