-
What Is Endpoint Security? EPP, EDR, and XDR Explained
- Key Data: Fronts of Attacks
- Why Endpoint Security Is Mandatory
- How Does Endpoint Security Work?
- Types of Endpoint Security: A Multi-Layered Approach
- Traditional Antivirus vs. Modern Endpoint Security
- Implementing Zero Trust for Endpoint Security
- Other Key Components
- Selecting the Optimal Endpoint Security Solution
- Strategic Endpoint Security: Challenges and Best Practices
- Endpoint Security FAQs
- What Is Endpoint Detection?
-
What Is Endpoint Security Software? How It Stops Cyberattacks
- Endpoint Security Software Explained
- Endpoint Security Software vs. Antivirus
- Core Components of Comprehensive Endpoint Security Software
- How Does Endpoint Security Software Protect a Network?
- What are the Key Features of Endpoint Security Software?
- EPP vs. EDR vs. XDR
- The Role of Threat Hunting in Endpoint Security
- Implementation Strategies for Enterprise Environments
- Defending Against Ransomware: A Use Case
- Endpoint Security Software FAQs
- What Is an Endpoint? Understand Devices, Risks & Security
- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
-
What is Endpoint Security Awareness Training?
- Understanding Security Awareness Training
- Endpoint Security Awareness Training Explained
- What Does Endpoint Security Awareness Training Cover?
- Why Is Security Awareness Training Important?
- How to Build an Effective Endpoint Security Awareness Training Program
- Industry Awareness Training Case Studies and Success Stories
- The Future of Endpoint Security Awareness Training
- Endpoint Security Awareness Training FAQs
-
What Is an Endpoint Protection Platform?
- Understanding Endpoint Protection Platforms (EPPs)
- The Importance of Endpoint Protection for Enterprises
- What Cybersecurity Practitioners and CISOs Need to Know About EPPs
- Traditional vs. Cloud Native EPPs
- EPP vs EDR: A Comparative Analysis
- Case Studies: Real-World Applications
- How to Choose the Best EPP
- Endpoint Protection Platform (EPP) FAQs
- What are the Types of Endpoint Security?
-
What Is Endpoint Security Antivirus?
- Endpoint Security Antivirus Explained
- Understanding Endpoints in Cybersecurity
- Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
- Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
- Key Components of a Comprehensive Endpoint Security Solution
- How Endpoint Security Antivirus Works
- Implementing and Optimizing Endpoint Security Antivirus
- Choosing the Right Endpoint Security Antivirus Solution
- Challenges and Future Trends in Endpoint Security
- Endpoint Security Antivirus FAQs
What Is Next-Generation Antivirus (NGAV)
Traditional signature-based antivirus is ineffective against advanced threats such as script-based, multi-vector and fileless attacks, as well as advanced ransomware. This leads to significant gaps in a company’s security posture. What’s more, virtual endpoints often lack broader contextual intelligence to ensure an effective enterprise security architecture.
Consequently, relying on traditional antivirus software is not enough to protect companies from unknown malware and threats.
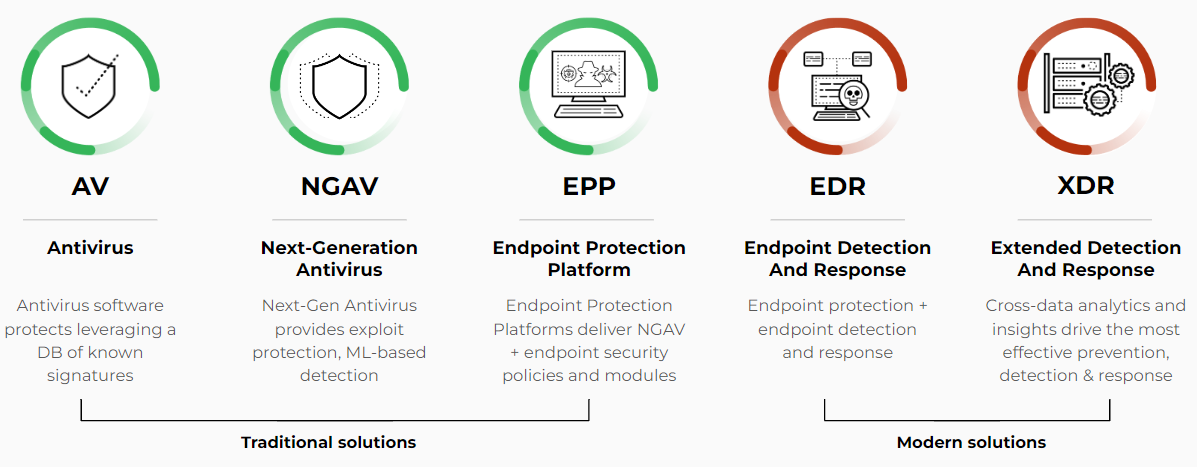
Endpoint security solutions available today
The Value and Benefits of NGAV
Advanced endpoint security solutions using machine learning and behavioral protection can offer companies far more sophisticated protection than traditional antivirus solutions. NGAV solutions can proactively detect and identify threats, including never-before-seen malware and ransomware. They can also use predictive analytics and behavioral protection to stop fileless threats like PowerShell abuse. Machine learning models check thousands of attributes of a file to identify both known and unknown threats.
These capabilities enable companies to prevent endpoint attacks and malware proactively, instead of just dealing with security-related incidents after the fact.
AI and Machine Learning in Modern NGAV
Today's next-generation antivirus solutions have evolved far beyond basic machine learning models to incorporate sophisticated artificial intelligence capabilities that fundamentally transform threat detection and prevention.
Deep Learning and Neural Networks Modern NGAV platforms utilize deep neural networks that can analyze millions of file attributes simultaneously, identifying malicious patterns that traditional signature-based systems would miss. These AI models continuously learn from global cyber threat intelligence, adapting to new attack techniques without requiring manual updates or signature deployments.
Real-Time Behavioral AI Advanced NGAV solutions employ behavioral AI that monitors process execution, file system changes, network communications, and registry modifications in real-time. This allows the system to detect and block malicious behavior even when attackers use legitimate tools or living-off-the-land techniques. The AI can distinguish between normal administrative activities and suspicious behavior patterns that indicate compromise.
Predictive Threat Intelligence AI-powered NGAV platforms integrate with global threat intelligence feeds to predict and prevent emerging attack vectors before they become widespread. Machine learning algorithms analyze threat actor tactics, techniques, and procedures (TTPs) to proactively identify and block new variants of malware families, even zero-day threats that have never been seen before.
Automated Response and Remediation Modern AI capabilities enable NGAV solutions to not only detect threats but automatically orchestrate response actions. This includes isolating infected endpoints, rolling back malicious changes, and coordinating with other security tools to contain threats across the enterprise without human intervention.
Why Companies Need to Protect Their Sensitive Data
While NGAV is a major step up from traditional antivirus, the endpoint security market has progressed significantly, and now offers solutions that bundle together NGAV with detection and response capabilities. Leading endpoint protection features are often included in solutions categorized as endpoint detection and response (EDR), or in the more comprehensive extended detection and response (XDR) category, which stitches together data from across sources to improve the fidelity of detections and the ease of investigations.
The reality is that enterprises can’t block 100% of attacks while maintaining business continuity, so they need to be able to detect, investigate and respond to threats as a critical second layer of defense behind their endpoint protection. For companies to get the best endpoint security, they need to fully protect their networks. They should look to deploy capabilities beyond those generally included in NGAV, such as the ability to:
- Identify and block endpoint attacks at all stages of the attack lifecycle.
- Gain holistic visibility across the entire organization, including endpoints, network, cloud and cloud assets.
- Coordinate between detection and prevention capabilities to deliver consistent security across the entire network.
- Safeguard all endpoints, regardless of operating system, whether an endpoint is on-site or remote, online or offline, connected to the company’s network or not.
- Protect both virtual and cloud environments.
- Take a proactive approach to security by combining multiple methods of prevention to automatically identify and stop potential security attacks, the execution of malicious programs and the exploitation of legitimate applications in real time. This includes limiting where executable files can run on an endpoint and customizing settings, if needed.
- Deliver more accurate security verdicts (e.g., malicious or benign) and minimize the number of false positive alerts.
- Simplify deployment and management with cloud-based security.
All of this can allow companies to dramatically shorten the time it takes to discover, hunt down, investigate and respond to potential security attacks. While EDR solutions can help organizations stop endpoint threats, cybersecurity teams must think beyond the endpoint and protect their entire organization holistically. That is why organizations should consider market-leading XDR solutions, rather than NGAV and EDR solutions, to protect their endpoints and their data.
For more information on XDR, visit the Cortex XDR product page.
