-
What Is Endpoint Security? EPP, EDR, and XDR Explained
- Key Data: Fronts of Attacks
- Why Endpoint Security Is Mandatory
- How Does Endpoint Security Work?
- Types of Endpoint Security: A Multi-Layered Approach
- Traditional Antivirus vs. Modern Endpoint Security
- Implementing Zero Trust for Endpoint Security
- Other Key Components
- Selecting the Optimal Endpoint Security Solution
- Strategic Endpoint Security: Challenges and Best Practices
- Endpoint Security FAQs
- What Is the Difference Between Advanced Endpoint Security and Antivirus (AV)?
-
What is Endpoint Security Awareness Training?
- Understanding Security Awareness Training
- Endpoint Security Awareness Training Explained
- What Does Endpoint Security Awareness Training Cover?
- Why Is Security Awareness Training Important?
- How to Build an Effective Endpoint Security Awareness Training Program
- Industry Awareness Training Case Studies and Success Stories
- The Future of Endpoint Security Awareness Training
- Endpoint Security Awareness Training FAQs
- What Is Endpoint Detection?
-
What Is Endpoint Security Software? How It Stops Cyberattacks
- Endpoint Security Software Explained
- Endpoint Security Software vs. Antivirus
- Core Components of Comprehensive Endpoint Security Software
- How Does Endpoint Security Software Protect a Network?
- What are the Key Features of Endpoint Security Software?
- EPP vs. EDR vs. XDR
- The Role of Threat Hunting in Endpoint Security
- Implementation Strategies for Enterprise Environments
- Defending Against Ransomware: A Use Case
- Endpoint Security Software FAQs
- What Is an Endpoint? Understand Devices, Risks & Security
-
What Is an Endpoint Protection Platform?
- Understanding Endpoint Protection Platforms (EPPs)
- The Importance of Endpoint Protection for Enterprises
- What Cybersecurity Practitioners and CISOs Need to Know About EPPs
- Traditional vs. Cloud Native EPPs
- EPP vs EDR: A Comparative Analysis
- Case Studies: Real-World Applications
- How to Choose the Best EPP
- Endpoint Protection Platform (EPP) FAQs
- What Is Next-Generation Antivirus (NGAV)
-
What Is Endpoint Security Antivirus?
- Endpoint Security Antivirus Explained
- Understanding Endpoints in Cybersecurity
- Why Endpoint Security Antivirus is Crucial for Modern Cybersecurity
- Endpoint Antivirus vs. Endpoint Security: What Is the Difference?
- Key Components of a Comprehensive Endpoint Security Solution
- How Endpoint Security Antivirus Works
- Implementing and Optimizing Endpoint Security Antivirus
- Choosing the Right Endpoint Security Antivirus Solution
- Challenges and Future Trends in Endpoint Security
- Endpoint Security Antivirus FAQs
What are the Types of Endpoint Security?
Endpoint cybersecurity is an essential and dynamic aspect of cybersecurity, continuously adapting to protect against an ever-growing range of threats. It is a vital shield in protecting the integrity and confidentiality of data across all endpoint devices within and outside of an organization's network.
There are various types of endpoint security that organizations can implement to protect their endpoints. The most effective solutions include:
- Endpoint threat prevention
- Next-generation anti-virus
- Endpoint exploit prevention
- Endpoint detection and response (EDR)
- Extended detection and response (XDR)
- Cloud workload security
- Device control
- Endpoint encryption
- Endpoint firewall
- Host intrusion prevention
- Data loss prevention (DLP)
- Internet of Things (IoT) security
- Insider threat protection
- Data classification
- Network Access Control (NAC)
- Uniform Resource Locator (URL) filtering
- Browser isolation
- Sandboxing
These technologies work together to provide robust security measures against unauthorized access, malware, and other cyberthreats that put an organization’s data at risk.
What is an Endpoint?
An endpoint is a device, virtual machine, or container that connects to a network and communicates with it. This can include standard devices like desktop computers and laptops. Still, the definition has expanded to include many other devices essential to personal and professional life in today's interconnected world.
Why is Endpoint Security Important?
Endpoint security is crucial due to various reasons. It protects against diverse threats, ensures data protection, mitigates insider threats, secures remote workforces, guards against evolving threats, helps comply with regulations, and prevents downtime and losses.
As companies increasingly adopt cloud-based services and remote working models, the perimeter of their network expands. This change has caused the role of endpoint security to evolve. Endpoint security now requires a combination of network security measures and cloud-based solutions to protect not only the devices within a physical office but also those scattered across different locations, accessing corporate resources remotely.
Traditional Endpoints
The most recognized endpoints include desktops, laptops, and workstations. These devices have been the primary focus of endpoint security for years, as they are common targets for malware, hacking attempts, and various cyberthreats due to their prevalent use in corporate and personal environments.
Mobile Devices
With the surge in mobile technology, smartphones and tablets have become ubiquitous. They are communication tools and gateways to corporate data and networks. This evolution has necessitated the expansion of endpoint security strategies to include these devices, ensuring they are protected against unauthorized access and malware.
IoT Devices
IoT devices, such as wearables, smart home devices, and industrial equipment, often collect and transmit sensitive data, making them attractive targets for cyberattacks. However, they often lack robust security features, posing unique security challenges.
Point-of-Sale Systems and Other Specialized Devices
Other endpoints include point-of-sale (POS) systems used in retail environments, medical devices in healthcare settings, and various types of sensors in industrial contexts. These specialized devices are critical for business operations and often contain sensitive data, thus requiring dedicated security measures.
Types of Endpoint Security Solutions
Various endpoint security solutions have been developed in the diverse cybersecurity landscape to address the myriad of threats organizations face. These solutions range from essential malware protection to advanced detection and response systems, each vital in a comprehensive security strategy.
Antivirus and Anti-Malware
One of the foundational elements of endpoint security is antivirus and anti-malware software. These solutions act as digital guardians, constantly scanning for malicious software. When they detect malware, they act, neutralizing the threat and keeping your endpoints safe.
Antivirus and anti-malware software rely on two primary methods for threat detection:
- Signature-based detection
- Behavior-based detection
Signature-based detection involves comparing files to a database of known malware signatures. If a match is found, the software takes action. On the other hand, behavior-based detection observes the behavior of files and applications. If something behaves suspiciously, it's flagged as a potential threat.
Anti-malware software, while similar in function, is often more focused on newer forms of malware, like ransomware, spyware, and adware. Together, these tools form the bedrock of endpoint security, offering essential protection for individual devices and the broader network.
Firewalls
Firewalls are like the gatekeepers of your network. They control the traffic entering and leaving your endpoints, ensuring only authorized communication occurs. They come in various forms, including network firewalls and host-based firewalls.
Different Types of Firewalls
Network firewalls operate at the network level, inspecting data packets and determining whether they should be allowed. On the other hand, host-based firewalls run on individual endpoints, offering an additional layer of protection by monitoring and filtering traffic at the device level.
Endpoint Detection and Response (EDR)
Moving beyond traditional antivirus, Endpoint Detection and Response (EDR) represents a more dynamic and proactive approach to cybersecurity. EDR solutions continuously monitor and gather data from endpoint devices, searching for anomalies and signs of malicious activity.
Unlike conventional antivirus software that relies on known threat signatures, EDR platforms use behavioral analysis and machine learning to detect and respond to threats in real time. This includes immediate containment of the infected endpoint, breach investigation, and remediation measures to prevent future attacks.
EDR solutions are particularly effective in identifying and mitigating sophisticated, targeted attacks that might bypass traditional security measures. Their in-depth approach to endpoint monitoring makes them crucial for organizations looking to bolster their cybersecurity defenses.
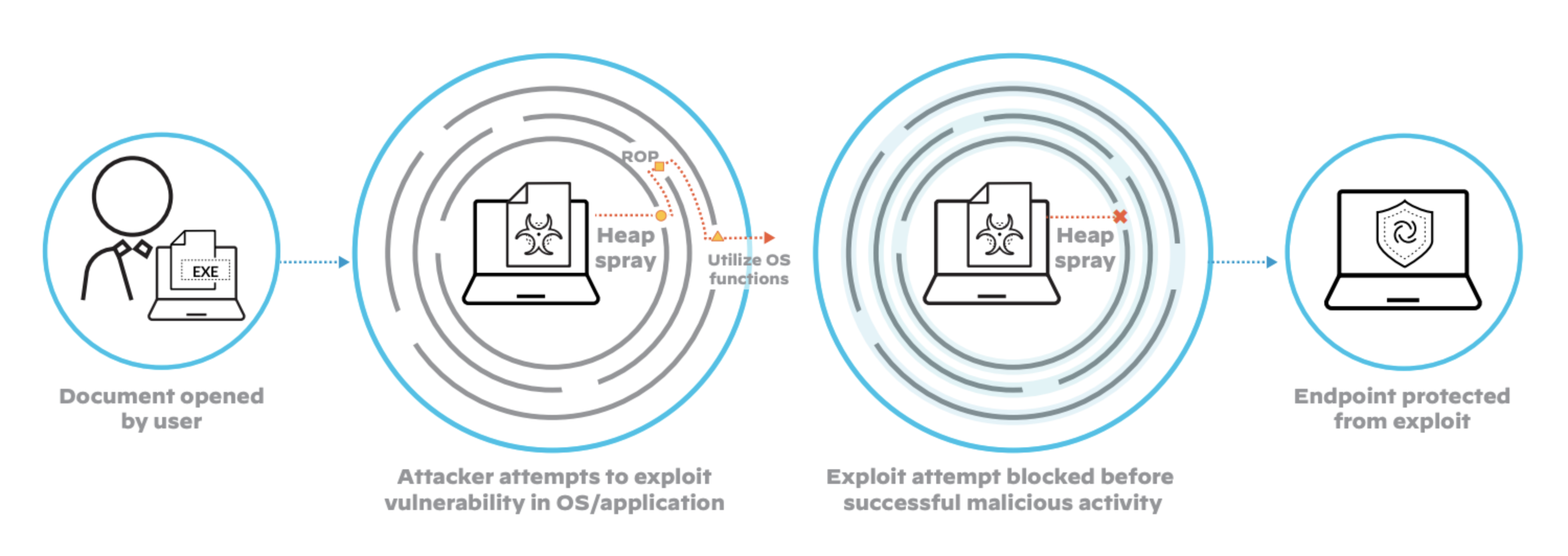
Figure 1: Focus on exploit techniques rather than the exploits themselves
Extended Detection and Response (XDR)
Extended Detection and Response (XDR) is a security solution that provides comprehensive threat detection, investigation, and response capabilities across various security layers, like email, endpoint, server, cloud workloads, and networks. XDR aims to provide a more integrated and holistic approach to threat detection and response instead of siloed or isolated security solutions. With visibility and analytics conducted across multiple security data sources, more attacks can be detected and remediated at the endpoint target.
XDR systems use technologies like machine learning, behavioral analysis, and big data analytics to detect sophisticated threats. XDR can identify anomalies that might indicate a security breach by analyzing patterns across different platforms and data sources.
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS)
IDS and IPS are like security guards for your endpoints. They actively look for signs of intrusion attempts and can even take action to prevent them. They are crucial for real-time network security, particularly for endpoint devices.
How They Work
Intrusion Detection Systems (IDS) are designed to monitor network traffic and identify potential security breaches by analyzing patterns or signatures of known attacks. These systems examine network traffic in real time, looking for any suspicious activity that could indicate an attempted intrusion.
IDS generates alerts when they detect such activity, notifying administrators or network security personnel. It is important to note that IDS do not actively block malicious traffic; instead, they generate alerts to alert security personnel to the potential threat.
On the other hand, Intrusion Prevention Systems (IPS) take it further by actively blocking potentially malicious traffic to prevent an attack. These systems analyze network traffic in real time and compare it to pre-defined rules or policies.
If any traffic matches these rules, IPS will block the traffic before reaching its intended destination. This proactive approach to network security can help prevent attacks before they occur, protecting critical systems and data.
Data Loss Prevention (DLP)
Data is often an organization's most valuable asset, making its protection crucial. DLP solutions are designed to prevent the unauthorized access or leakage of sensitive data.
Methods Used
DLP solutions employ various methods to protect data. These include content inspection, contextual analysis, and monitoring data transfers. DLP solutions can accurately identify and prevent potential breaches by understanding the context in which data is used.
Application Whitelisting and Blacklisting
Think of application whitelisting and blacklisting as traffic cops for software. They decide which applications are allowed to run on an endpoint.
How They Control Software Execution
Application whitelisting, as the name suggests, allows only approved applications to run, while blocking everything else. This method is based on trust, where a pre-approved list of applications is maintained and only those applications can execute on the endpoint. This way, application whitelisting ensures that only authorized software can run on the system, minimizing the risk of malware infections and other security threats.
On the other hand, blacklisting blocks known malicious applications while permitting everything else. This approach works by maintaining a list of known malicious applications and preventing them from running on the endpoint. The blacklisting method is less restrictive than whitelisting since it allows any application that is not on the blacklist to run. However, it requires frequent updates to the blacklist to keep up with new threats and is less effective against zero-day attacks.
Endpoint Encryption
Endpoint encryption is like sealing your data in a vault. It ensures that even if an attacker gains access to your endpoint, they can't decipher the data without the encryption key.
Encryption Methods
Various encryption methods, such as full disk and file-level encryption, protect data on endpoints. These methods are highly effective in preventing data breaches.
Network Access Control (NAC)
NAC solutions ensure that only authorized devices can access your network. They help maintain the integrity of your network by verifying the identity and compliance of connecting devices.
Authentication and Device Profiling
NAC solutions often require users and devices to authenticate before granting access. They also profile devices to ensure they meet security standards. If a device doesn't comply, access is denied.
Behavior Analysis and Anomaly Detection
Detecting Anomalies
These solutions establish a baseline of normal behavior for each endpoint. When they detect deviations from this baseline, they raise alerts. This proactive approach helps identify potential threats before they cause damage.
Mobile Device Management (MDM)
With the proliferation of smartphones and tablets, securing mobile devices is crucial. MDM solutions provide control and security for these devices.
Policies and Controls
MDM solutions enable organizations to enforce policies, control app installations, and remotely wipe lost or stolen devices. This level of control helps mitigate potential risks associated with mobile devices.
IoT Security
The Internet of Things (IoT) has revolutionized how we interact with our surroundings by enabling a wide range of devices connected to the Internet, including smart home appliances, wearable devices, and industrial sensors. However, these connected devices are vulnerable to security threats, such as hacking and data breaches, which can have profound implications for individuals and businesses.
IoT security solutions are therefore essential to safeguard these devices and protect the sensitive information they collect and transmit. These security solutions use various technologies, such as encryption, authentication, and access control, to ensure that the devices are secure, reliable, and compliant with industry standards.
Protecting Connected Devices
IoT security solutions safeguard IoT devices from botnet attacks and data breaches. They ensure these devices don't become weak links in your security chain.
Insider Threat Detection
Not all threats come from external sources. Insider threats, whether intentional or unintentional, can be equally damaging. Insider threat detection solutions monitor user activity within the organization to identify and mitigate potential risks.
Identifying and Mitigating Risks
These solutions analyze user behavior, looking for signs of malicious intent or accidental breaches. Organizations can take corrective action by identifying insider threats early before significant damage occurs.
Vulnerability Management
Vulnerabilities in software and systems are like open doors for attackers. Vulnerability management solutions help organizations identify and patch these weaknesses before they can be exploited.
Prioritizing and Patching
Vulnerability management solutions prioritize vulnerabilities based on their severity and potential impact. This enables organizations to focus on patching the most critical vulnerabilities first.
Selecting the Optimal Endpoint Security Solutions
At Palo Alto Networks, we understand that choosing the right endpoint security solutions is pivotal in your cybersecurity journey. Our experience and commitment to excellence empower us to guide this critical matter.
Tailoring Endpoint Security
When it comes to endpoint security, there's no one-size-fits-all solution. Every organization is unique, with its industry, data sensitivity, and budget constraints. Recommendations for navigating this crucial decision are as follows:
- Industry Insight: Begin by assessing the specific demands of your industry. Different sectors face distinct cybersecurity challenges. Palo Alto Networks has extensive experience in securing a wide array of industries, and our solutions are tailored to meet sector-specific needs.
- Data Sensitivity: Consider the sensitivity of your data. Some organizations handle highly confidential information, while others deal with less critical data. Palo Alto Networks can help you identify and prioritize data protection requirements, ensuring your most valuable assets are safeguarded effectively.
- Budget Consciousness: We understand the importance of managing costs without compromising security. Palo Alto Networks offers a range of solutions designed to provide robust endpoint security at various budget levels. Our flexible approach ensures that you get the best value for your investment.
- Layered Defense: Our cybersecurity philosophy advocates for a layered defense approach. Combining multiple security measures can significantly enhance your endpoint protection. Palo Alto Networks offers integrated security solutions that work seamlessly to provide comprehensive defense against many threats.