- What is a Public Cloud Firewall?
-
What Makes a Strong Firewall?
- User Identification and Access Management
- Credential Theft and Abuse Mitigation
- Application and Control Function Safety
- Encrypted Traffic Security
- Advanced Threat Defense and Cyberattack Prevention
- Mobile Workforce Protection
- Cloud Environment Security Enhancement
- Management Centralization and Security Capability Integration
- Task Automation and Threat Prioritization
- Strong Firewall FAQs
- What Is Firewall Configuration? | How to Configure a Firewall
- What Is Firewall as a Service (FWaaS)? | A Complete Guide
- What Is an Internal Firewall?
- What Is a Virtual Firewall?
- What Is a Perimeter Firewall?
- What Is a Host-Based Firewall?
- What Is a Distributed Firewall?
- What Are Firewall Rules? | Firewall Rules Explained
-
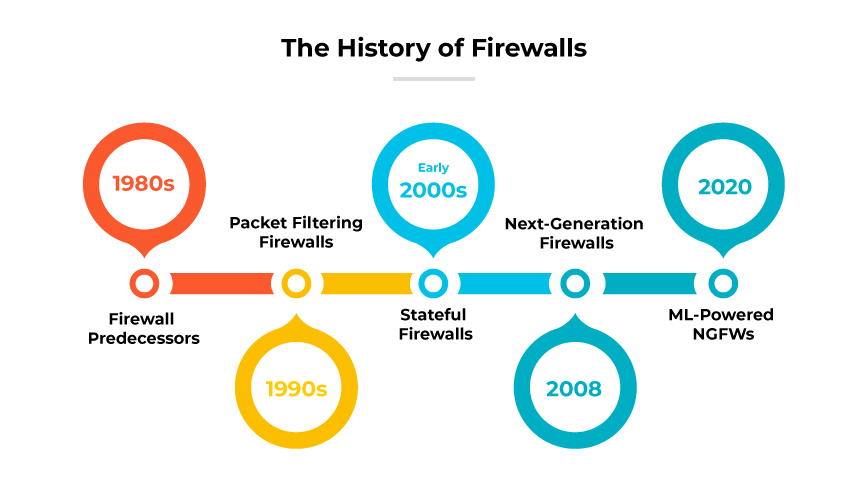
The History of Firewalls | Who Invented the Firewall?
- Firewall History Timeline
- Ancient History-1980s: Firewall Predecessors
- 1990s: First Generation of Firewalls—Packet Filtering Firewalls
- Early 2000s: Second Generation of Firewalls—Stateful Firewalls
- 2008: Third Generation of Firewalls—Next-Generation Firewalls
- 2020: Fourth Generation of Firewalls—ML-Powered NGFWs
- History of Firewalls FAQs
-
IPS. vs. IDS vs. Firewall: What Are the Differences?
- What Is a Firewall?
- What Is an Intrusion Detection System (IDS)?
- What Is an Intrusion Prevention System (IPS)?
- What Are the Differences Between a Firewall, IDS, and IPS?
- What Are the Similarities Between a Firewall, IDS, and IPS?
- Can a Firewall and IDS or IPS Work Together?
- IDS vs. IPS vs. Firewall FAQs
-
3 Virtual Firewall Use Cases
- Layer 3 vs Layer 7 Firewall: What Are the Differences?
-
How to Troubleshoot a Firewall | Firewall Issues & Solutions
- What are the most common firewall issues?
- How to troubleshoot a firewall
- Step 1: Know your troubleshooting tools
- Step 2: Audit your firewall
- Step 3: Identify the issue
- Step 4: Determine traffic flow
- Step 5: Address connectivity issues
- Step 6: Resolve performance issues
- Step 7: Maintain your firewall
- Why firewall testing is critical and how to do it
- Step 1: Review firewall rules
- Step 2: Assess firewall policies
- Step 3: Verify access control lists (ACLs)
- Step 4: Perform configuration audits
- Step 5: Conduct performance testing
- Step 6: Log and monitor traffic
- Step 7: Validate rule effectiveness
- Step 8: Check for policy compliance
- Firewall troubleshooting tips, tricks, and best practices
- Firewall issues FAQs
-
What Is Firewall Management? | A Comprehensive Guide
- Why is firewall management important?
- What are the main types of firewalls?
- What are the key components of firewall management?
- Who should be responsible for managing firewalls?
- What are the main firewall management challenges?
- Top 6 best practices for firewall management
- How to choose the right firewall management system for your needs
- Firewall management FAQs
- What Is a Stateful Firewall? | Stateful Inspection Firewalls Explained
- What Is a Proxy Firewall? | Proxy Firewall Defined & Explained
- What Is a Packet Filtering Firewall?
- What Is a Network Firewall?
- What Does a Firewall Do? | How Firewalls Work
- What Are the Benefits of a Firewall?
- Types of Firewalls Defined and Explained
-
Hardware Firewalls vs. Software Firewalls
- What Is a Hardware Firewall and How Does It Work?
- Benefits of Hardware Firewalls
- What Is a Software Firewall and How Does It Work?
- Benefits of Software Firewalls
- What Are the Differences Between Hardware Firewalls & Software Firewalls?
- Hardware vs. Software Firewalls
- What Are the Similarities Between Hardware Firewalls & Software Firewalls?
- Hardware Firewalls vs. Software Firewalls FAQs
-
Key Firewall Best Practices
- Harden and Configure Firewalls Properly
- Adopt a Customized, Phased Deployment Strategy
- Enhance and Regularly Update Firewall Protocols
- Ensure Rigorous Traffic Control
- Regularly Review and Update Access Controls
- Implement a Comprehensive Logging and Alert Mechanism
- Establish Backup and Restoration Protocols
- Align Policies with Compliance Standards
- Subject Firewalls to Regular Testing
- Conduct Routine Firewall Audits
- FAQs
- What Is a Container Firewall?
What Are the Top Firewall Features? | Traditional & NGFWs
The main features of firewalls can be broken down into those found in traditional and next-generation firewall solutions, including:
- Packet filtering
- Stateful inspection
- Network address translation (NAT)
- Logging and monitoring
- Access control
- Advanced threat prevention
- Advanced URL filtering
- DNS security
- IoT security
- Next-generation CASB
These features work together to filter out unauthorized access and threats from external sources while managing and monitoring traffic. Using both foundational security measures and advanced capabilities, firewalls are able to operate as a crucial barrier against a wide array of cyber threats.
How do firewalls work?
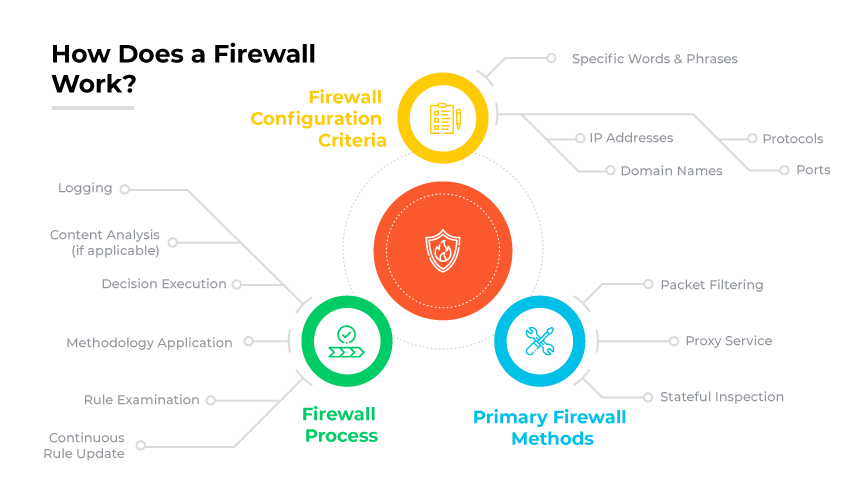
Before diving into the main features found in today’s firewalls, it’s worth taking a moment to establish how firewalls actually function.
Firewalls are essentially gatekeepers for the network. They manage and monitor data flow between the network and the internet.
Here’s how a firewall works:
A firewall establishes a barrier at the network's entry points. This is where security policies determine whether traffic should be allowed or blocked. The process is vital for protecting networks from unauthorized access and cyber threats.
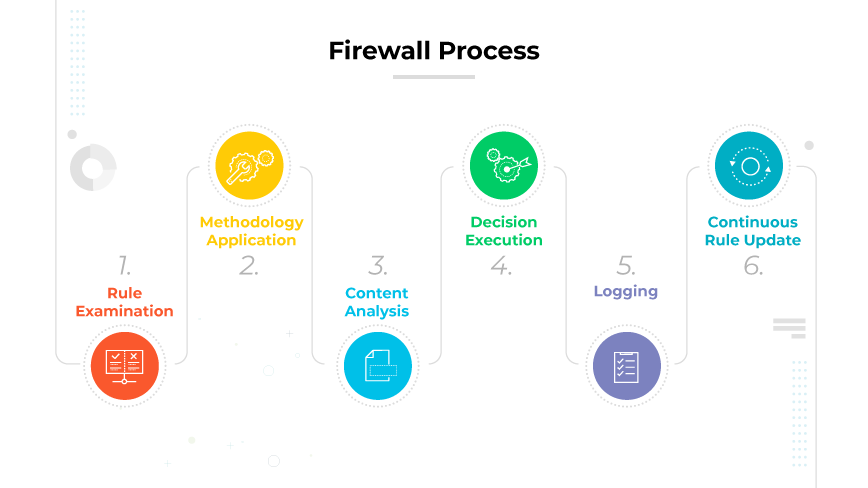
Firewalls, whether hardware or software, work using three main methods:
- Packet filtering: An access control mechanism that screens small data units (packets) against a predetermined rule set.
- Proxy service: Here, the proxy firewall acts as an intermediary. Instead of permitting direct communication of data packets between the user and the internet, the proxy fetches the data for the user and then relays it, preventing direct system access.
- Stateful inspection: Stateful inspection firewalls track outgoing packets and compare incoming responses to their database of active sessions. They approve only those that match a valid corresponding outbound packet.
At a basic level, firewalls use predetermined rules to inspect incoming and outgoing data packets.
Firewall rules can be based on:
- Source and destination IP addresses
- Domain names
- Protocols
- Ports
- Specific content within the data packets
By applying these rules, firewalls effectively block harmful traffic while allowing legitimate communications to pass through.
What are the main traditional firewall features?
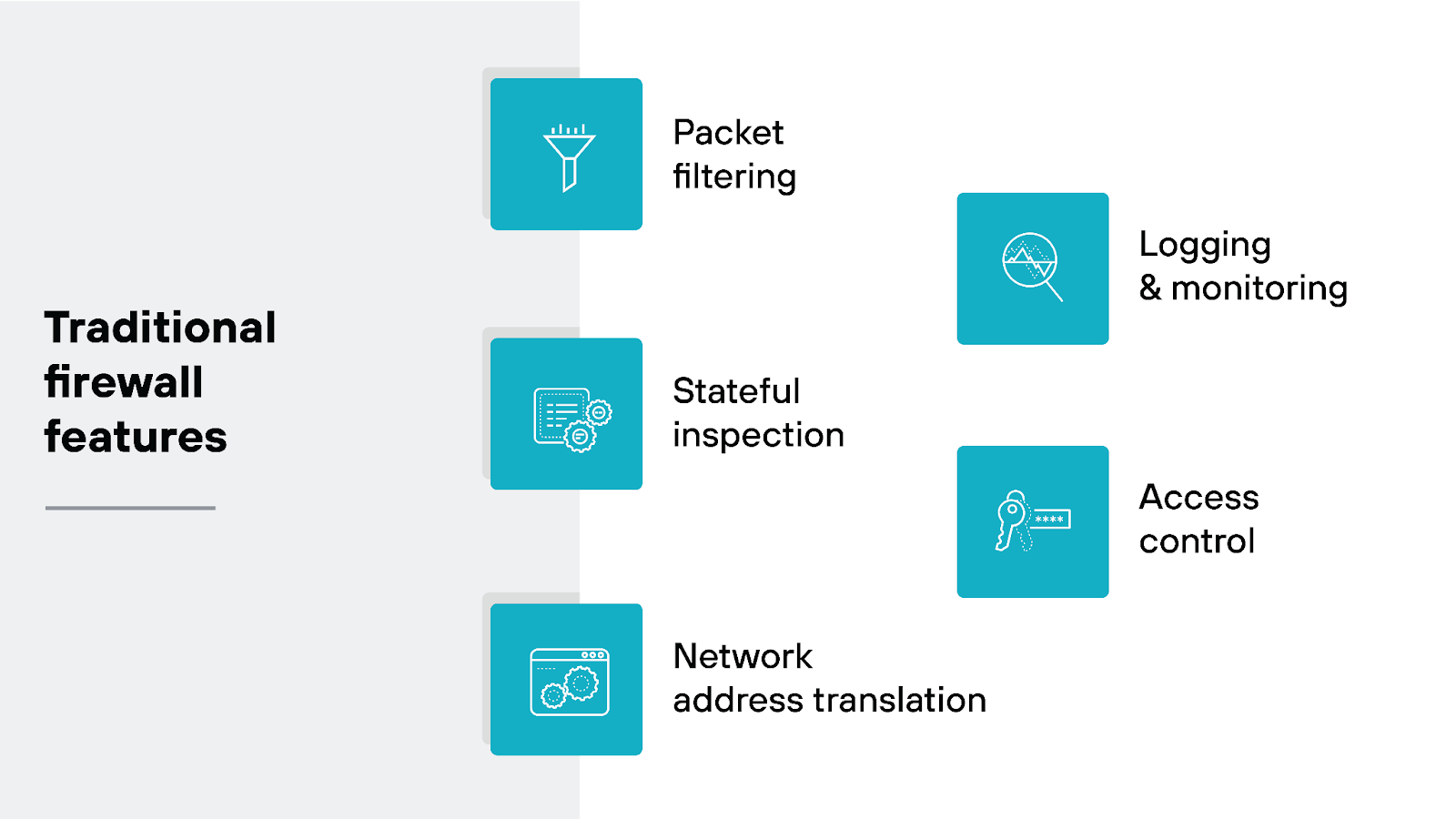
Traditional firewall solution features are basically the backbone of network security. These are the functionalities found in early firewall solutions that are still important today.
Basic firewall features include:
- Packet filtering
- Stateful inspection
- Network address translation (NAT)
- Logging and monitoring
- Access control
Together, these features create the network security foundation for ensuring that only authorized and safe communications are allowed through.
Packet filtering
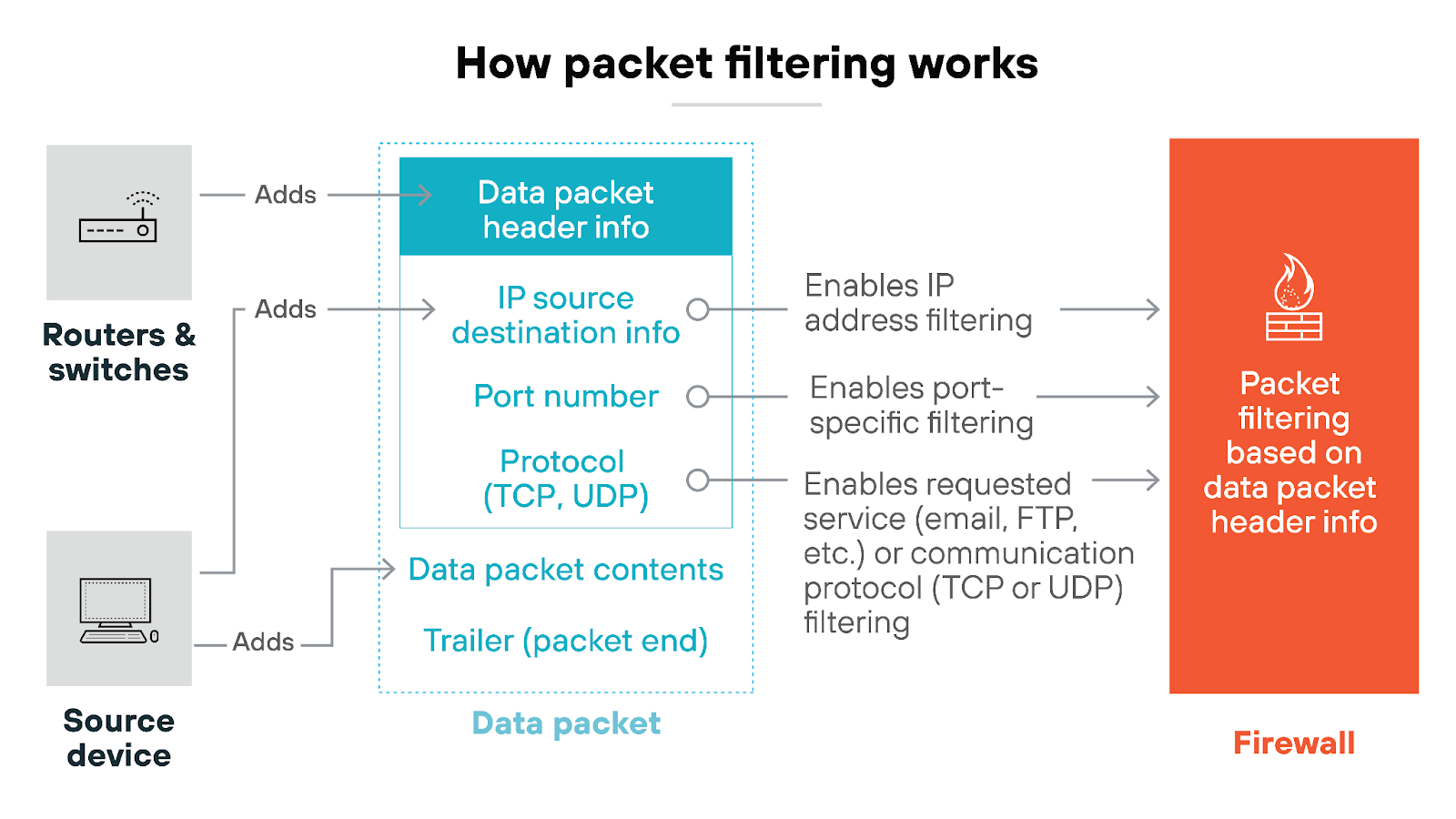
Packet filtering is the process of evaluating data packets as they pass through a firewall. Based on predetermined criteria, like source and destination IP addresses or port numbers, the firewall decides whether to allow or block each packet.
Think of packet filtering like a network traffic checkpoint. Every data packet attempting to enter or leave the network has to pass through.
More specifically, the firewall scrutinizes each packet's header. The header contains important details such as IP addresses and port numbers. Which determines whether the packet should be allowed to continue to its destination or be rejected based on the rules defined in the firewall.
Here’s how:
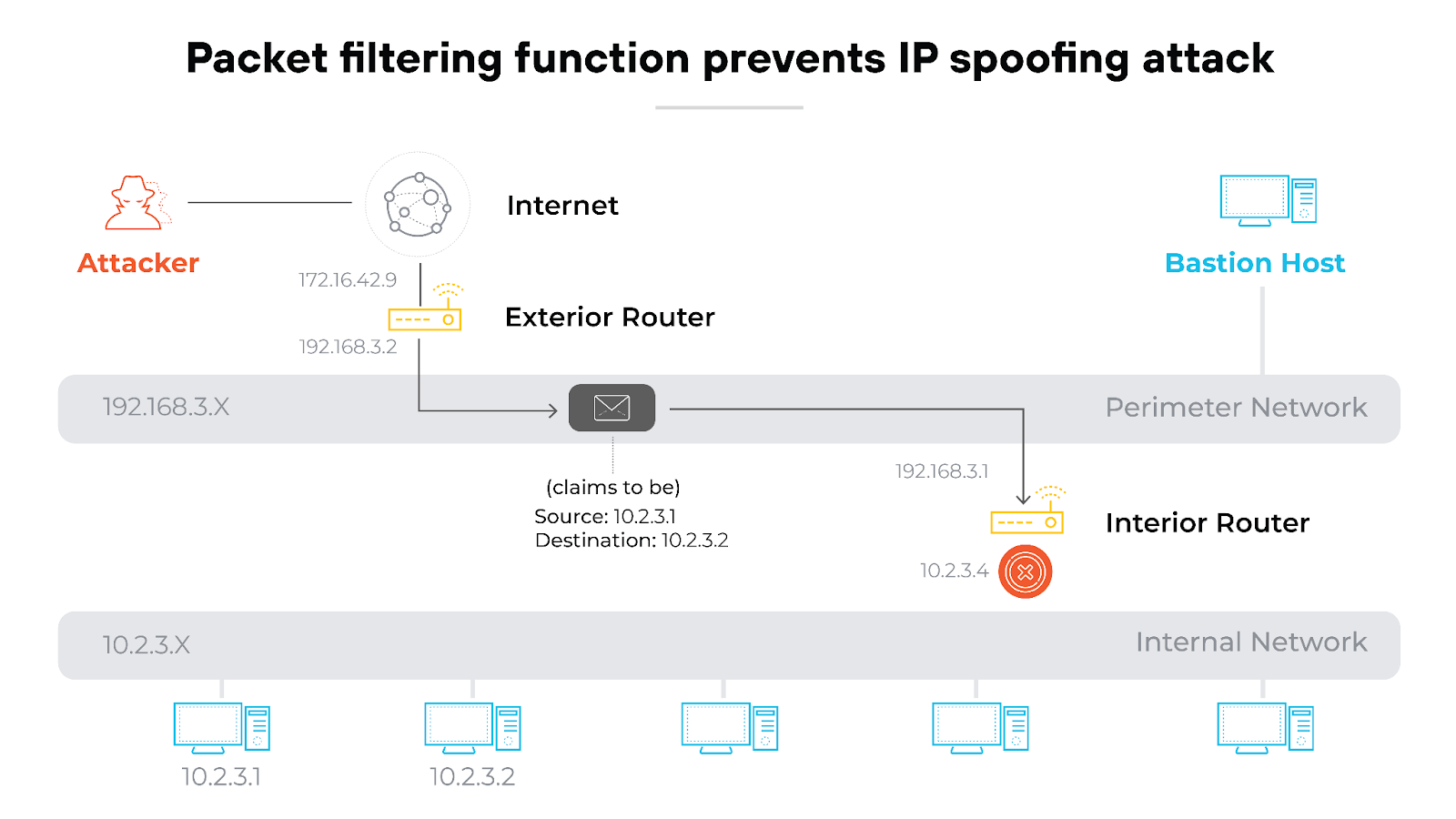
For example: Let's say a packet shows up claiming to come from a trusted source, but the source IP has been flagged previously for suspicious activity. The firewall recognizes the discrepancy through its predefined security rules, and immediately identifies the packet as a spoof. It then drops the packet before it can penetrate the network.
Like this:
While packet filtering is a basic form of firewall protection, it’s still essential even in modern network security strategies. It provides the first line of defense by eliminating packets that don't meet simple, yet crucial, criteria quickly.
However:
It's important to note that packet filtering alone isn’t a sufficient measure to take on more sophisticated threats. Which is why it's commonly integrated with other, more advanced types of firewall technologies like next-generation firewalls (NGFW) and intrusion prevention systems (IPS).
Further reading: What Is a Packet Filtering Firewall?
Stateful inspection
Stateful inspection is another fundamental feature of traditional firewalls. And it’s crucial for monitoring and managing the traffic that flows through a network.
Unlike simple packet filtering, stateful inspection tracks each connection's ongoing state and context. This makes the process more like a conversation versus isolated exchanges.
So, stateful inspection is a dynamic process. It tracks connections by logging various details such as source and destination IP addresses, port numbers, and the sequence and acknowledgment numbers involved in the communication.
This is what it looks like in practice:
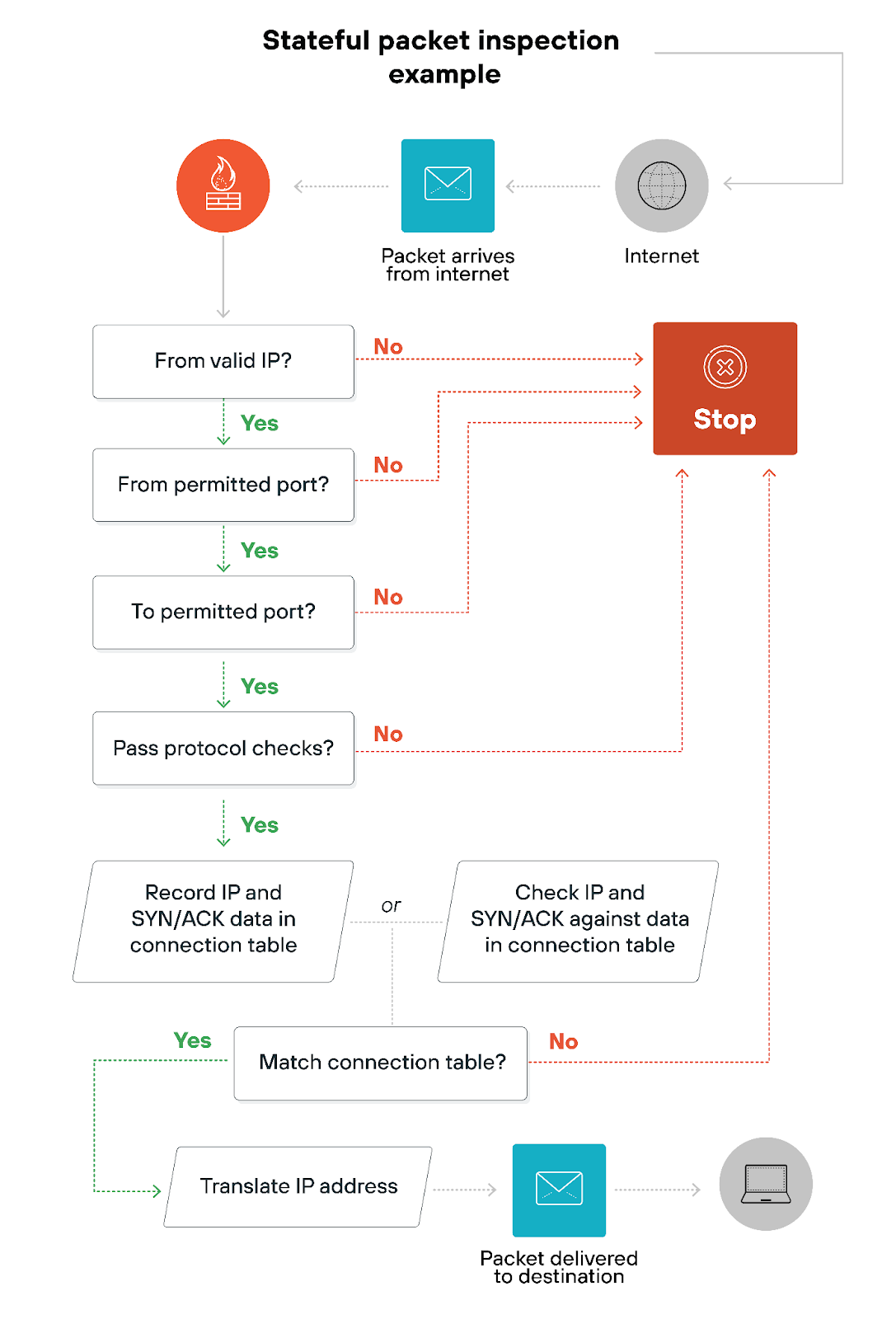
Stateful inspection is not unlike a vigilant receptionist that remembers the flow of visitors, checking each against a list of expected guests.
It examines every packet that attempts to enter the network, referencing a state table, such as this example below, that logs active connections:
Source address |
Source port |
Destination address |
Destination port |
Connection state |
|---|---|---|---|---|
192.168.2.150 |
1042 |
198.51.100.25 |
80 |
Established |
192.168.2.151 |
1045 |
203.0.113.45 |
443 |
Established |
192.168.2.152 |
1049 |
192.0.2.55 |
25 |
Established |
10.45.34.67 |
2035 |
198.51.100.30 |
80 |
Established |
10.45.34.68 |
2040 |
203.0.113.50 |
8080 |
Established |
172.16.84.90 |
2123 |
192.0.2.60 |
22 |
Established |
172.16.84.91 |
2150 |
198.51.100.35 |
443 |
Established |
10.10.30.45 |
2222 |
203.0.113.55 |
80 |
Established |
If a packet belongs to an established connection, it passes through seamlessly. If it doesn't match or seems out of context, the firewall blocks it.
Why is this method so effective, even for today’s firewall products?
Well, by maintaining a connection context, stateful inspection can identify and block packets that don't belong. Even if they appear harmless on the surface. And that prevents unauthorized access and attacks that rely on forging or hijacking legitimate sessions.
Plus: Because it reduces the need to inspect every packet in detail once a connection is established as safe, it improves the network's performance and reduces latency.
Further reading: What Is a Stateful Inspection Firewall?
Network address translation (NAT)
Network address translation, or NAT, enhances network flexibility and security.
Essentially, NAT allows multiple devices on a private network to access the internet using a single public IP address. It’s important for conserving limited IP addresses while maintaining each device’s ability to reach online resources.
NAT works by modifying the IP address information in packet headers as they pass through a router or firewall. This adjustment allows outbound packets from a private network to appear as though they originate from a public IP address.
In return, responses from the internet are directed back to the appropriate device on the private network.
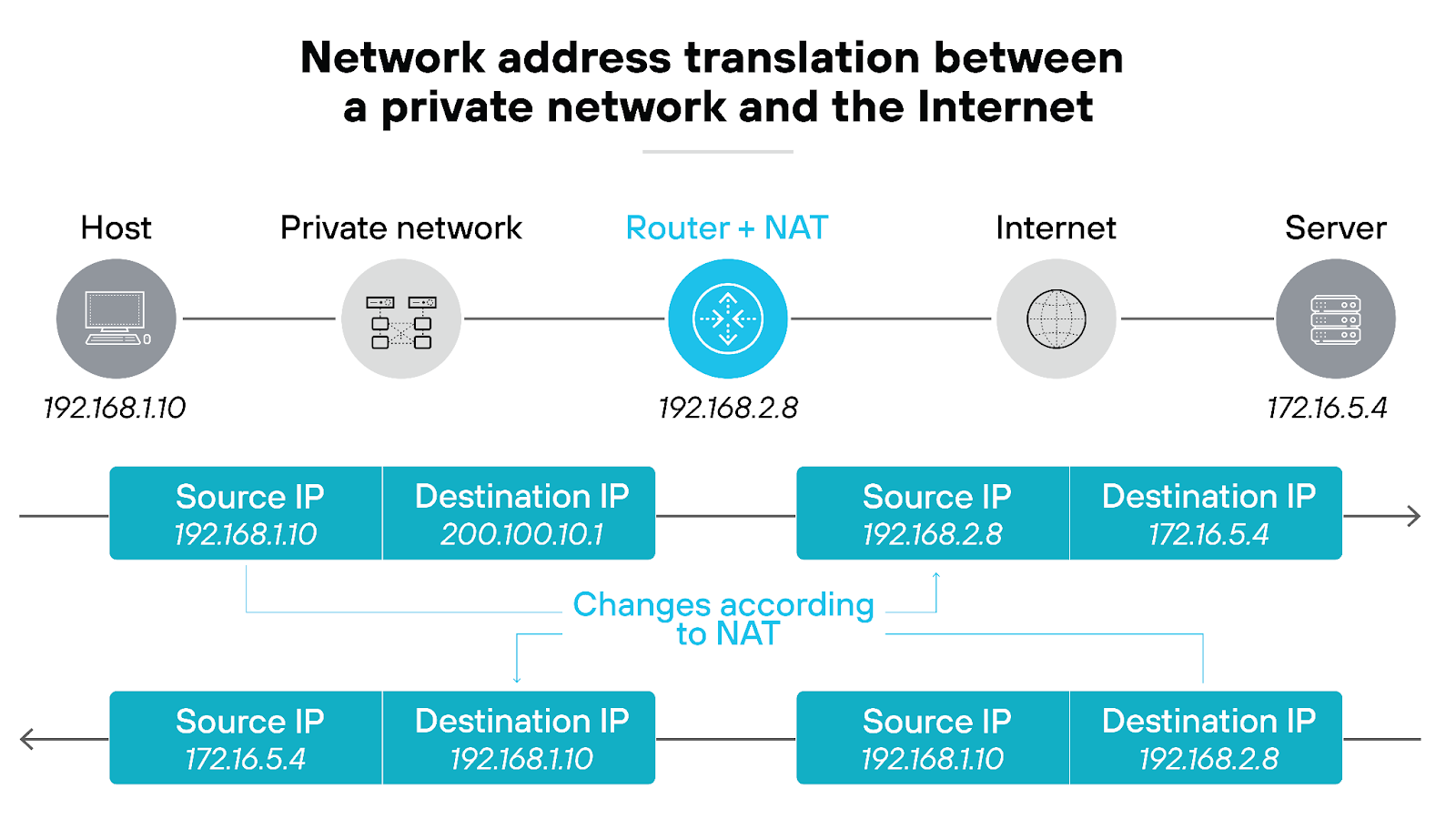
NAT maximizes the efficient use of public IP addresses. But it also adds a layer of security by keeping internal network addresses hidden from the outside world. Basically, NAT acts as a buffer between internal networks and potential external
threats—making unauthorized access more challenging.
For businesses, NAT provides an easy, cost-effective solution to manage internal internet access without the need for multiple public IP addresses. The functionality is integrated within firewalls to ensure all data flows are appropriately handled.
Logging and monitoring
Logging and monitoring are essential firewall functions. Together, they provide insights into network activity and security threats. Essentially, logging and monitoring features act as a comprehensive record-keeping and observation system for network traffic.
Firewalls log data just about every packet that passes through, noting details like source and destination IP addresses, port numbers, timestamps, and whether the traffic was allowed or blocked based on existing security rules.
This creates a detailed record that admins can review to understand traffic patterns and identify potential security breaches or unusual activities.
A firewall log looks like this:
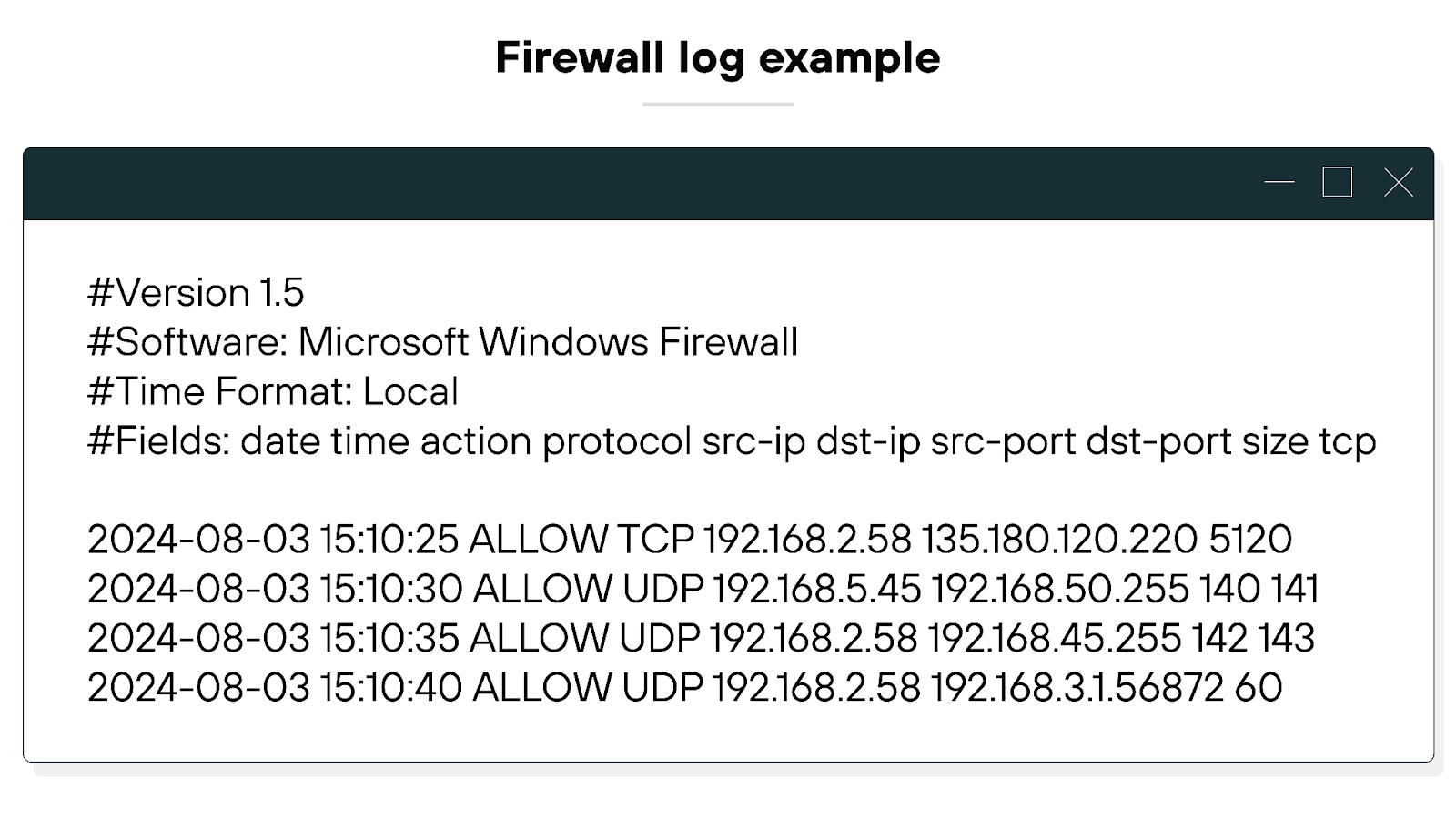
Monitoring, on the other hand, involves the real-time analysis of this data.
It helps in detecting anomalies as they occur, allowing network admins to react swiftly to possible threats. And being able to respond immediately makes it a lot easier to minimize damage from attacks and maintain network integrity.
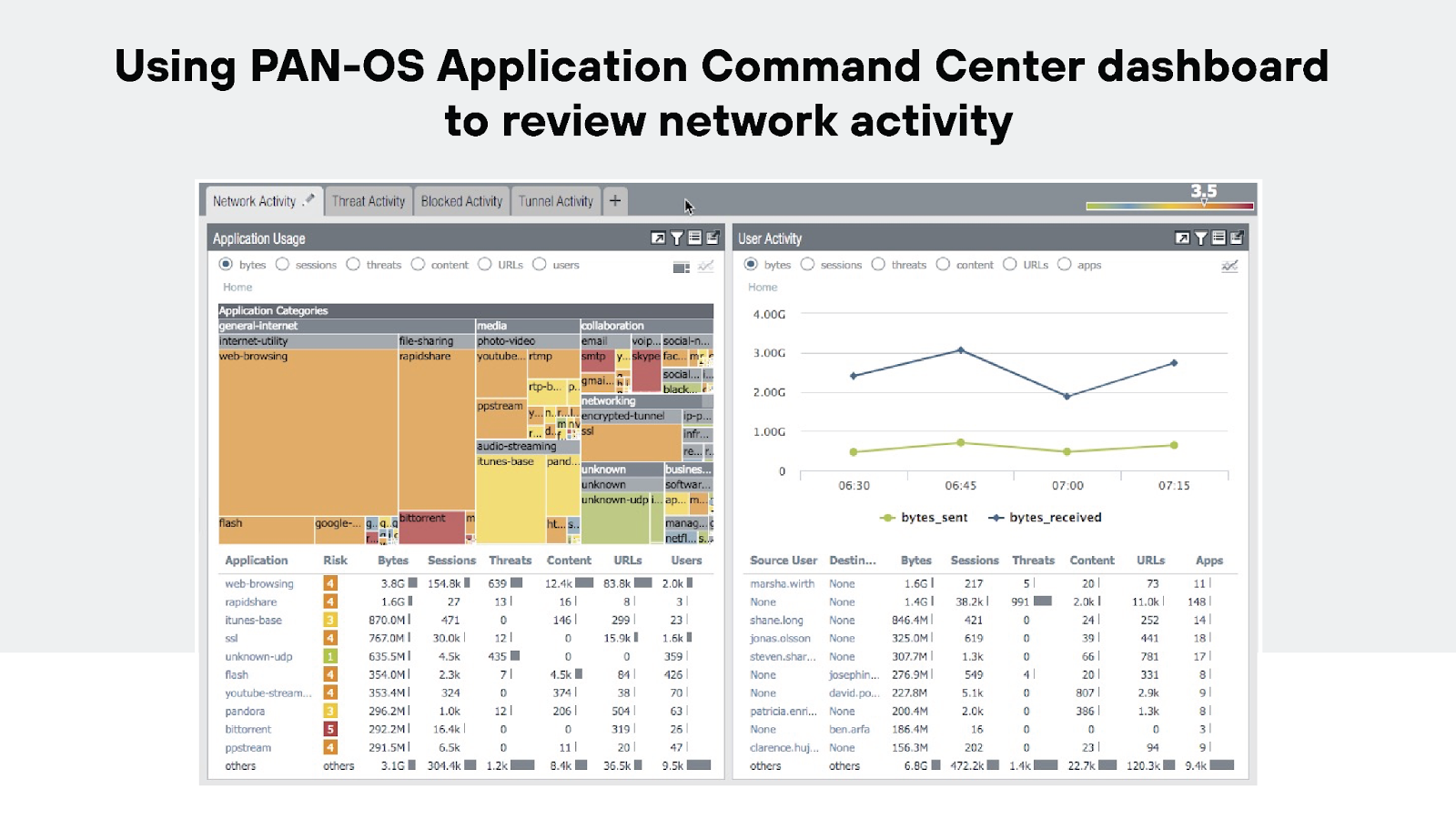
Here’s why logging and monitoring are so important.
Together, they provide a double-layered security approach. Logging offers a historical account that can be crucial for audits, forensic analysis, and compliance with security policies. And monitoring ensures ongoing vigilance against threats, helping admins stay a step ahead.
Not to mention: the dual approach also supports network performance optimization by analyzing traffic flow and user behavior.
Access control
Access control is another longstanding, fundamental firewall feature.
In keeping with the goal of many firewall functions, access control determines which traffic should be allowed or blocked based on predefined security rules. Controlling access supports the security of the network, and it also ensures that only legitimate users and data can flow in and out.
Access control in a firewall involves several steps:
First, the firewall examines each incoming and outgoing packet against a set of rules—these could include source and destination IP addresses, protocols, ports, and even time of day.
If a packet matches an allowed rule, it passes through the firewall. If not, it’s blocked.
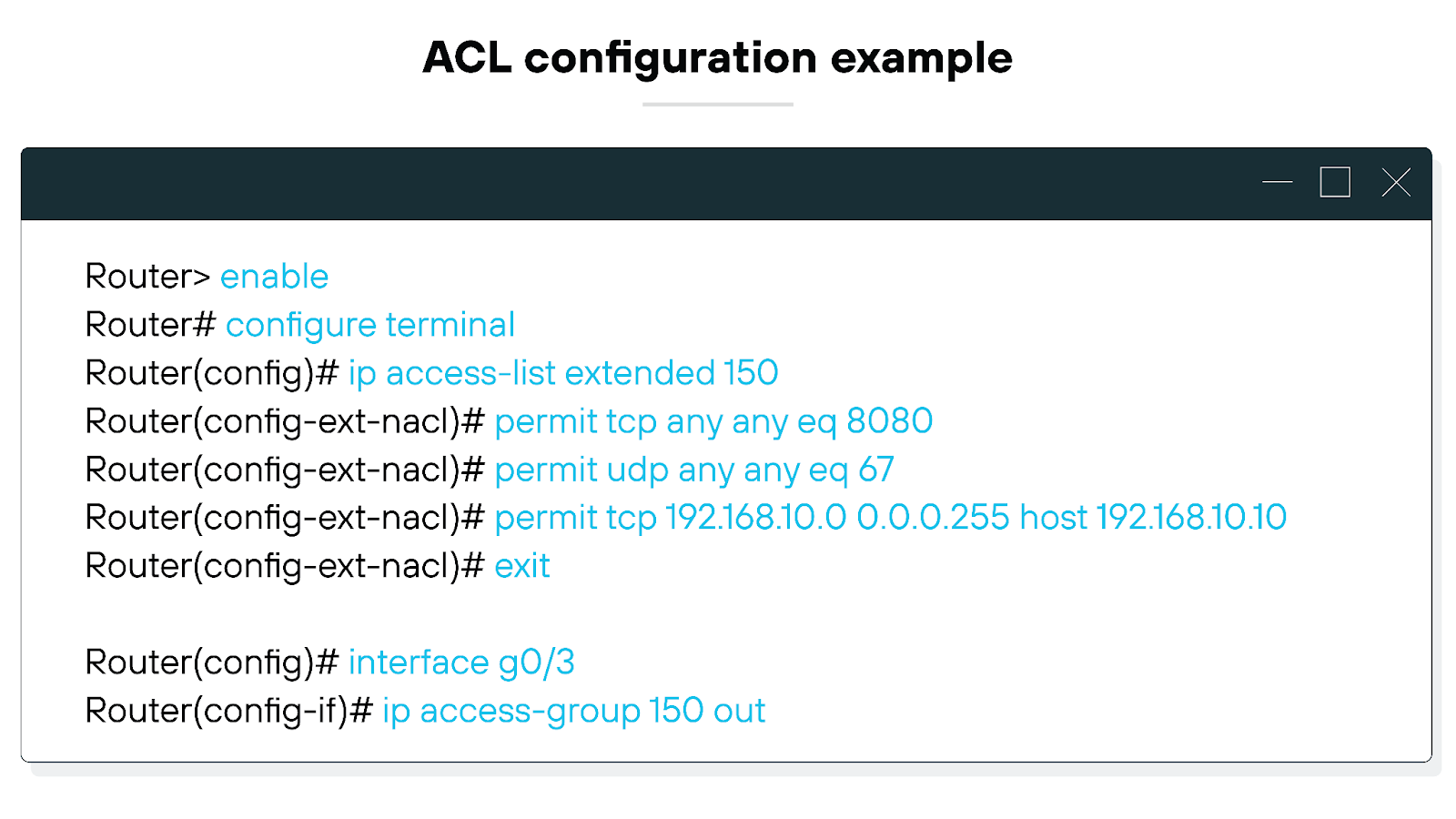
Why is this important?
Because access control helps prevent attackers from exploiting vulnerabilities within the network. It ensures that sensitive areas of the network are only accessible to authorized users. And that significantly reduces the risk of data breaches.
Also, it allows network admins to enforce policies that align with organizational security standards. Which helps to maintain a secure, efficient network environment.
In practice, access control within firewalls is continuously refined and updated to adapt to new threats and changes within the network. It's a dynamic tool that provides a critical security layer.
What are the main next-generation firewall (NGFW) features?
The genesis of firewall technology is rooted in age-old methods of physical defense. All the way back when people first began building walls to stop intruders. The real history of firewalls began in the 1980s with basic packet filtering firewalls, continually evolving into the modern next generation firewall of today.
As technology and business evolve, protection methods have to adapt.
It’s important to note that traditional firewalls do provide basic defense, but modern firewalls, or next-generation firewalls, including ML-powered NGFWs, reflect today's advanced digital threats. These firewalls blend proven, durable functionalities with new technologies for better, more effective network security.
NGFW products include modern firewall features ranging from application awareness and SSL inspection to threat intelligence and deep packet inspection (DPI).
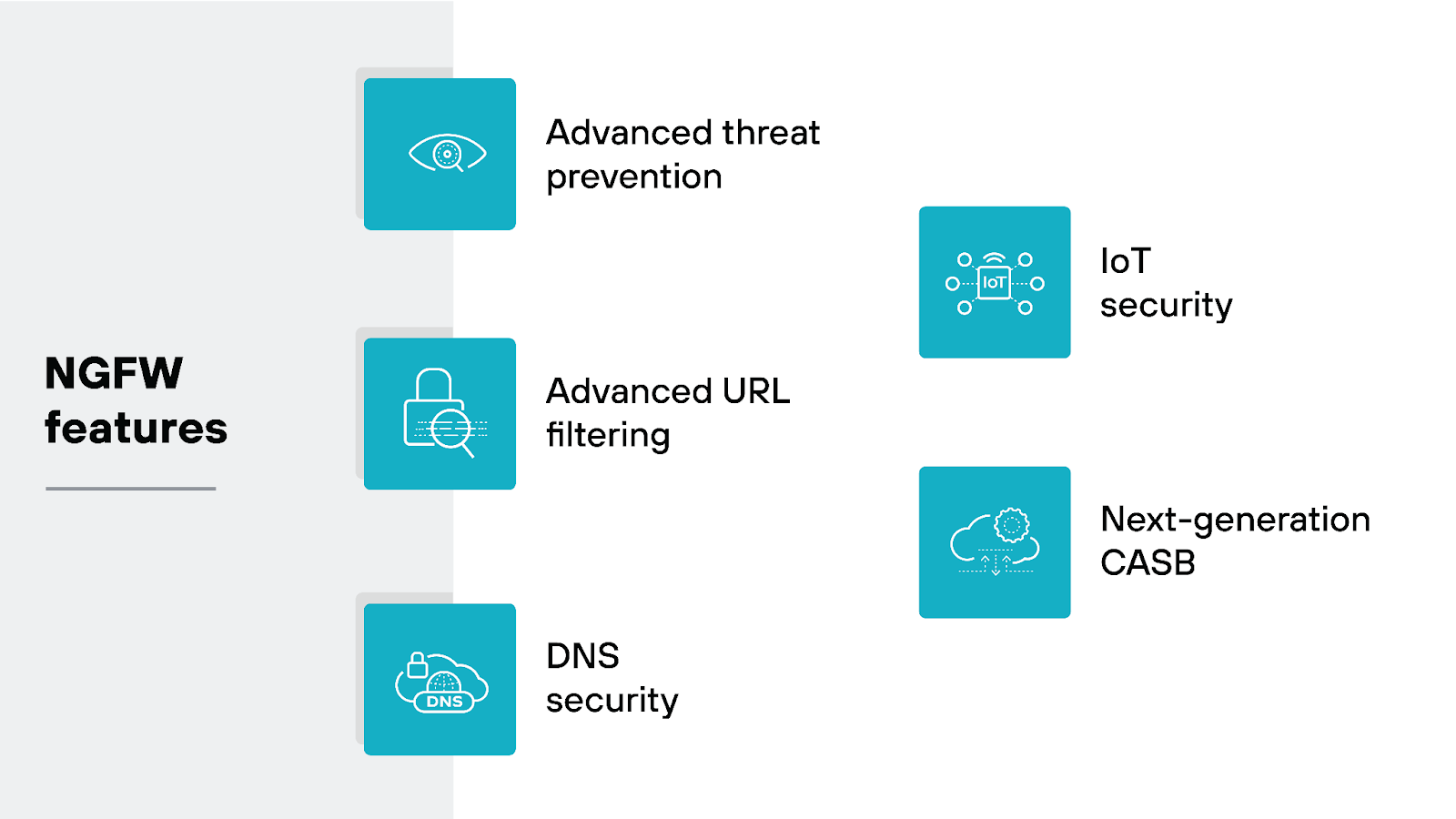
The primary NGFW features include:
- Advanced threat prevention
- Advanced URL filtering
- DNS security
- IoT security
- Next-generation CASB
Advanced threat prevention
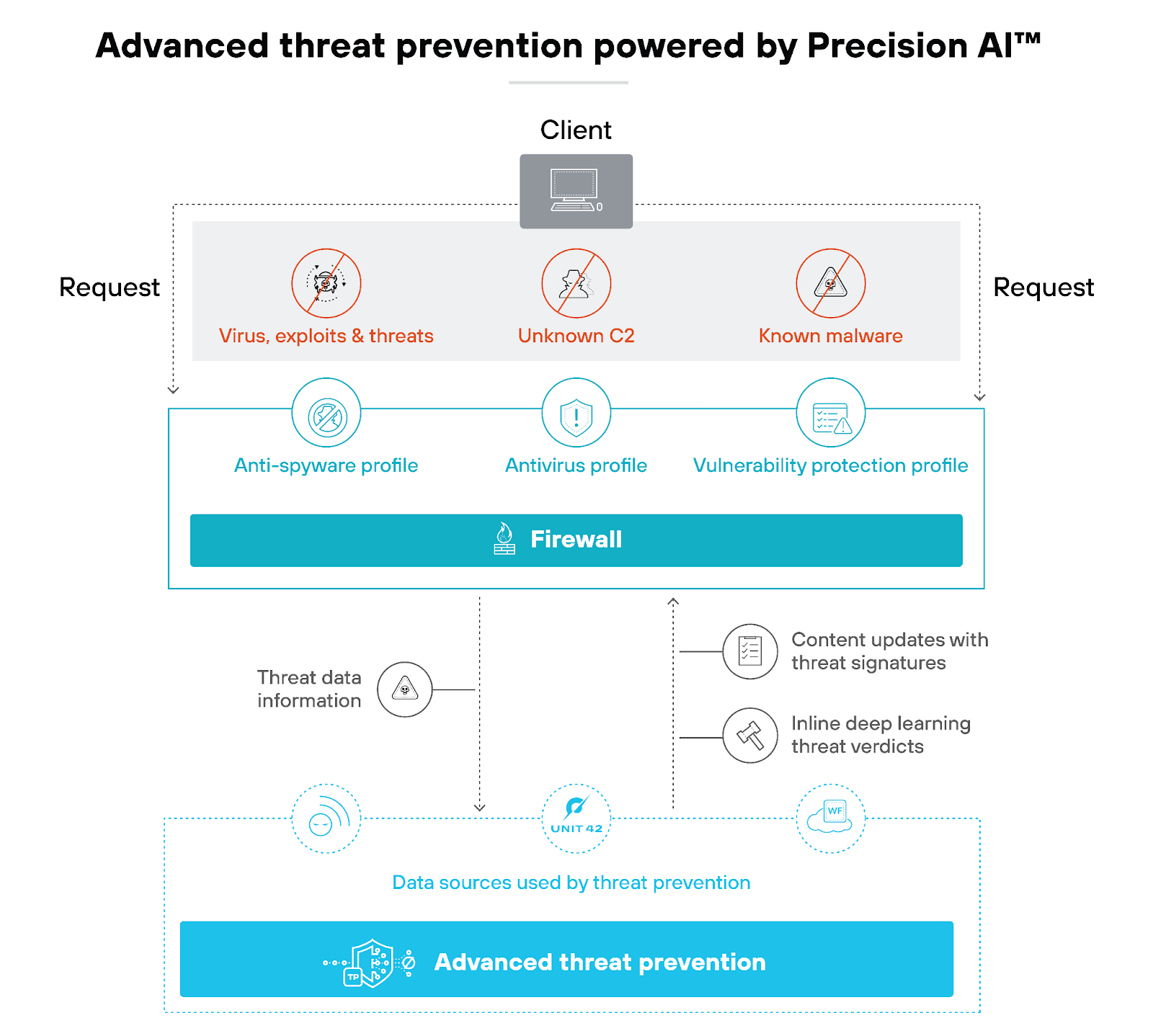
Advanced threat prevention (ATP) is a key feature of NGFWs. ATP goes beyond traditional security measures with multiple layers of defense to detect, analyze, and block malicious activities before they can cause harm.
ATP incorporates modern technologies like machine learning and behavior analysis to identify and counteract malware that evades standard detection.
It works by scrutinizing network traffic and files in real-time. Then it applies a combination of signature-based, heuristic, and behavioral techniques to pinpoint suspicious patterns and activities.
The multifaceted approach allows ATP to provide comprehensive protection against both known and emerging threats.
This is significant because the threat actors of today evolve their tactics at a previously unthinkable rate. And traditional security solutions simply can’t keep up.
ATP addresses this gap by continuously updating detection mechanisms with the latest threat intelligence. This way, the firewall can adapt to new vulnerabilities and attack methods.
This dynamic capability is vital for protecting sensitive data and maintaining network integrity against complex attacks like ransomware, zero-day exploits, and advanced persistent threats (APTs).
Advanced URL filtering
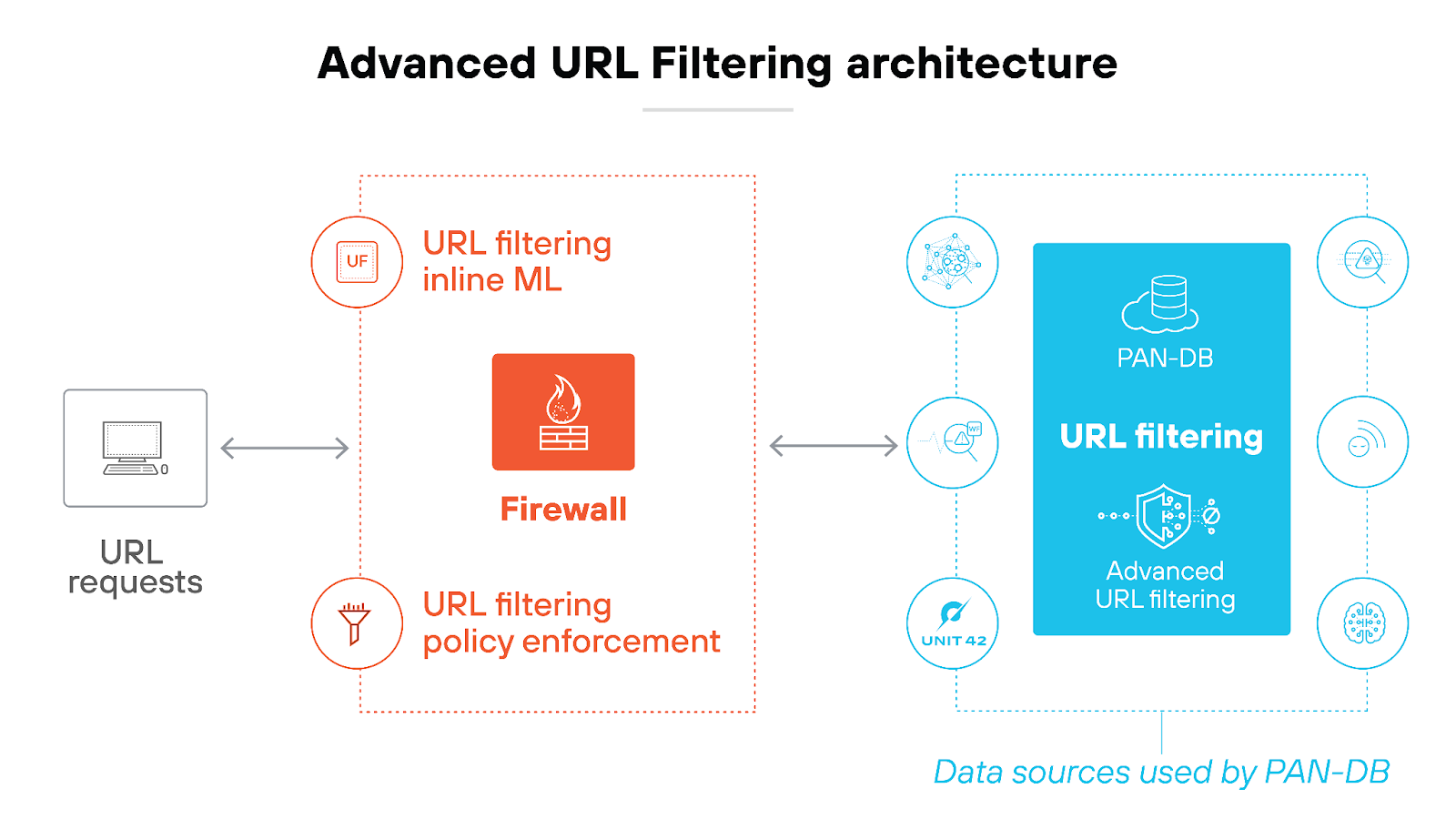
Advanced URL filtering in NGFWs is a critical security feature that blocks access to malicious websites.
It assesses URLs in real-time, using updated databases and dynamic analysis to categorize and evaluate web traffic. This process helps identify and prevent access to sites known for hosting malware, phishing, and other cyber threats.
Here’s how it works:
The system uses machine learning to adapt to emerging threats, analyzing new or unknown websites to detect harmful content swiftly. If a site poses a risk, the firewall restricts access—which protects the network from potential security breaches.
Advanced URL filtering is vital for enforcing safe web browsing practices. It also supports compliance with organizational policies, and protects sensitive data.
It also provides valuable insights into how web traffic moves through the network. These insights help admins manage web usage more effectively. And make it easier to identify and address potential issues before they escalate.
Further reading: What Is URL Filtering?
DNS security
The objective of DNS security is to secure the Domain Name System (DNS), which is fundamental to internet communication. DNS security ensures that the DNS infrastructure is reliable and efficient. Which prevents attacks that could redirect users to malicious sites or disrupt network services.
DNS security is so critical because DNS is a primary target for cyber attacks, mostly because of its essential role in network addressing. Which means that securing it helps prevent a wide range of attacks, including cache poisoning and denial of service (DoS).
DNS security uses predictive analytics and machine learning to thwart sophisticated attacks leveraging DNS. Its tight integration with the firewall automates protections, provides deeper insights into threats, and eliminates the need for separate tools.
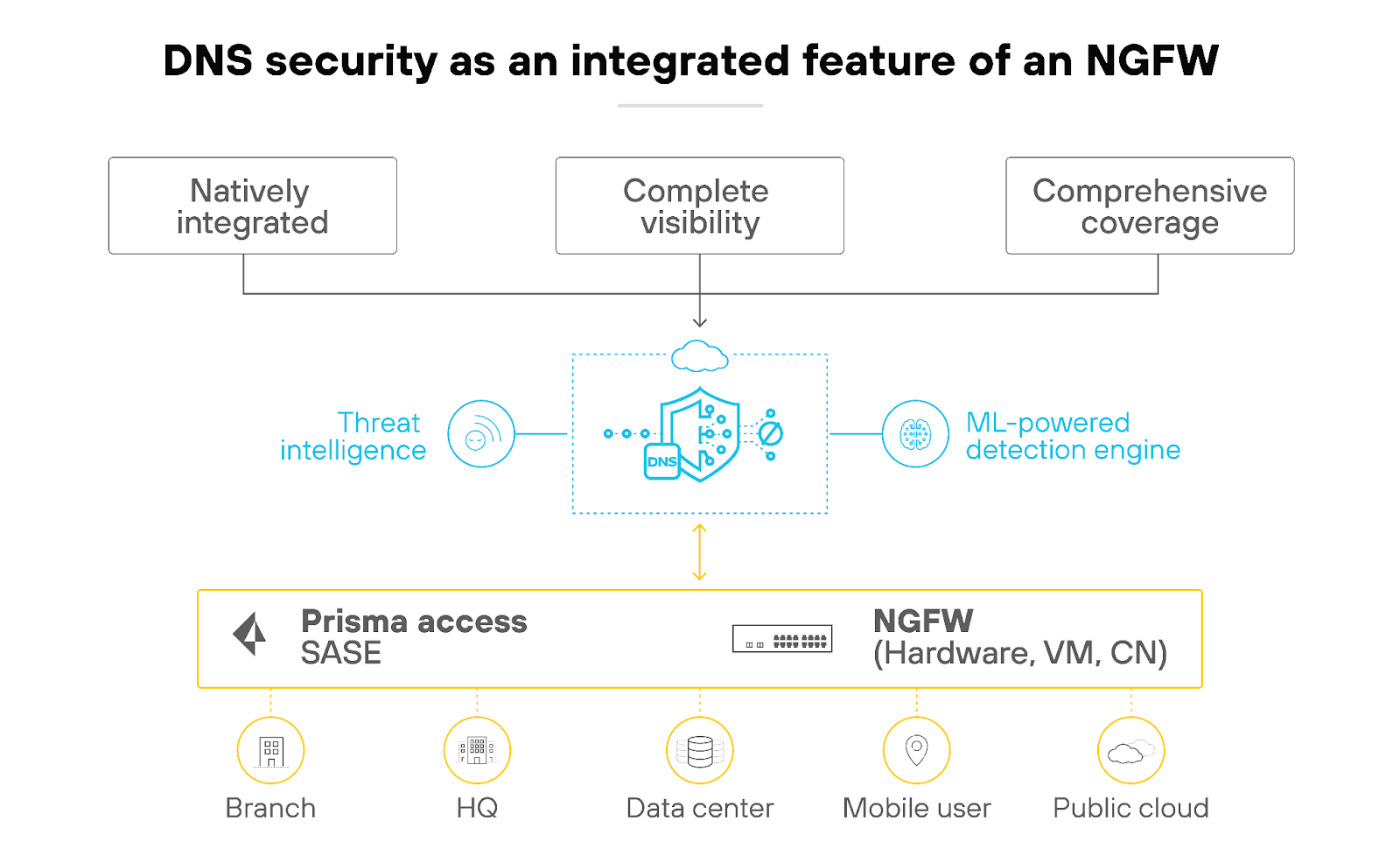
DNS security works by monitoring DNS requests and responses. It uses advanced algorithms to detect anomalies and potential threats. By applying security measures like DNSSEC (Domain Name System Security Extensions), NGFWs can authenticate DNS responses. And that ensures their integrity and blocks forged information that could lead to phishing or malware infections.
Enhanced DNS security within NGFWs also includes filtering to prevent access to known malicious domains. Which reduces the risk of malware infections and data breaches.
IoT security
IoT security within NGFWs is a crucial feature designed to protect the vast array of interconnected devices within modern networks. As the Internet of Things (IoT) expands, so does the potential for security vulnerabilities. And that makes robust IoT security mechanisms indispensable.
Plus, with the proliferation of IoT devices in both corporate and consumer environments, the attack surface has significantly increased. Devices often have varying levels of security, making some highly vulnerable to attacks.
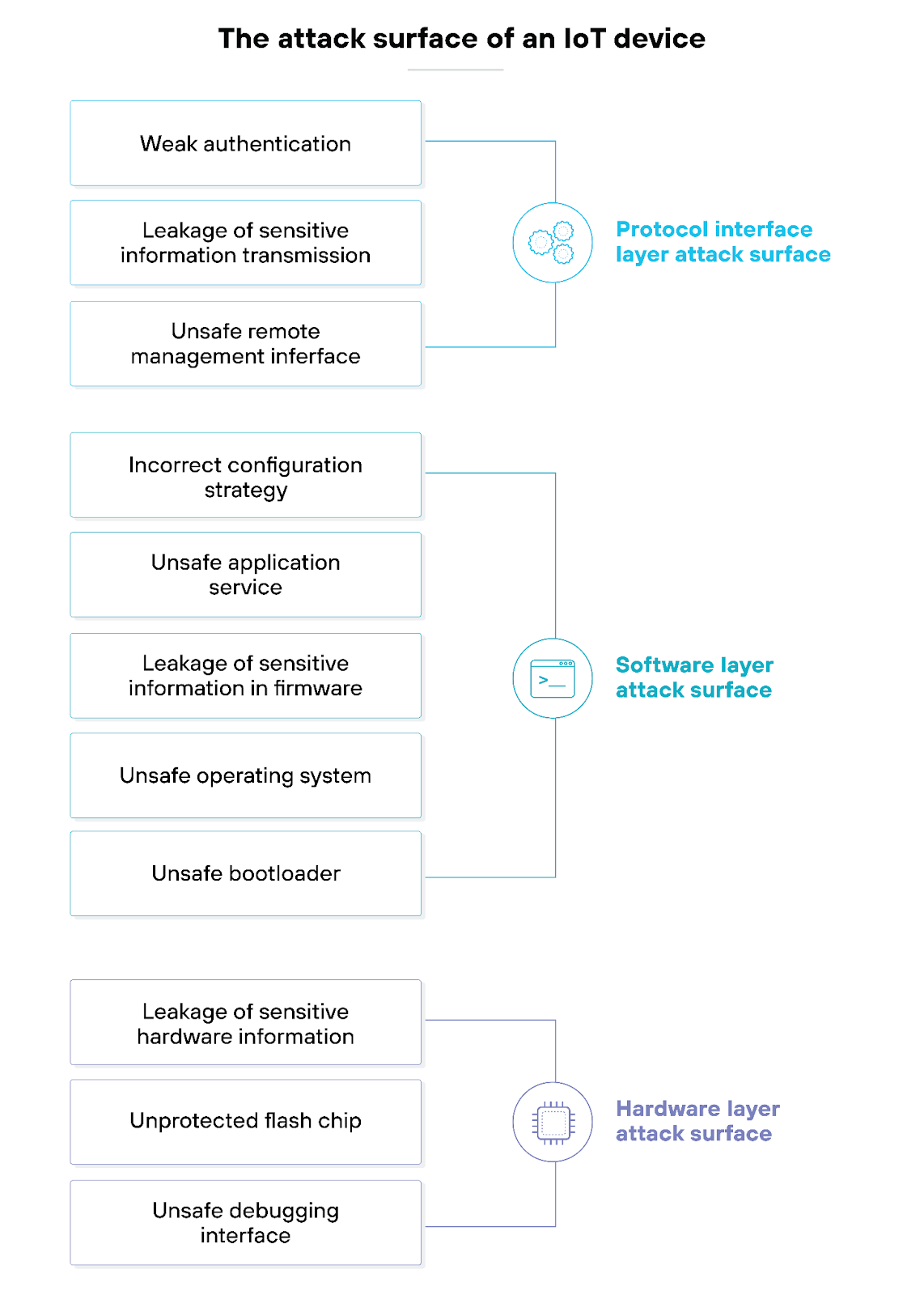
IoT security within NGFWs offers a robust Zero Trust security approach for IoT devices, combining visibility, prevention, and enforcement.
With the integration of machine learning, modern firewalls can segment networks based on context. This reduces risk and protects both IoT and IT devices from various threats.
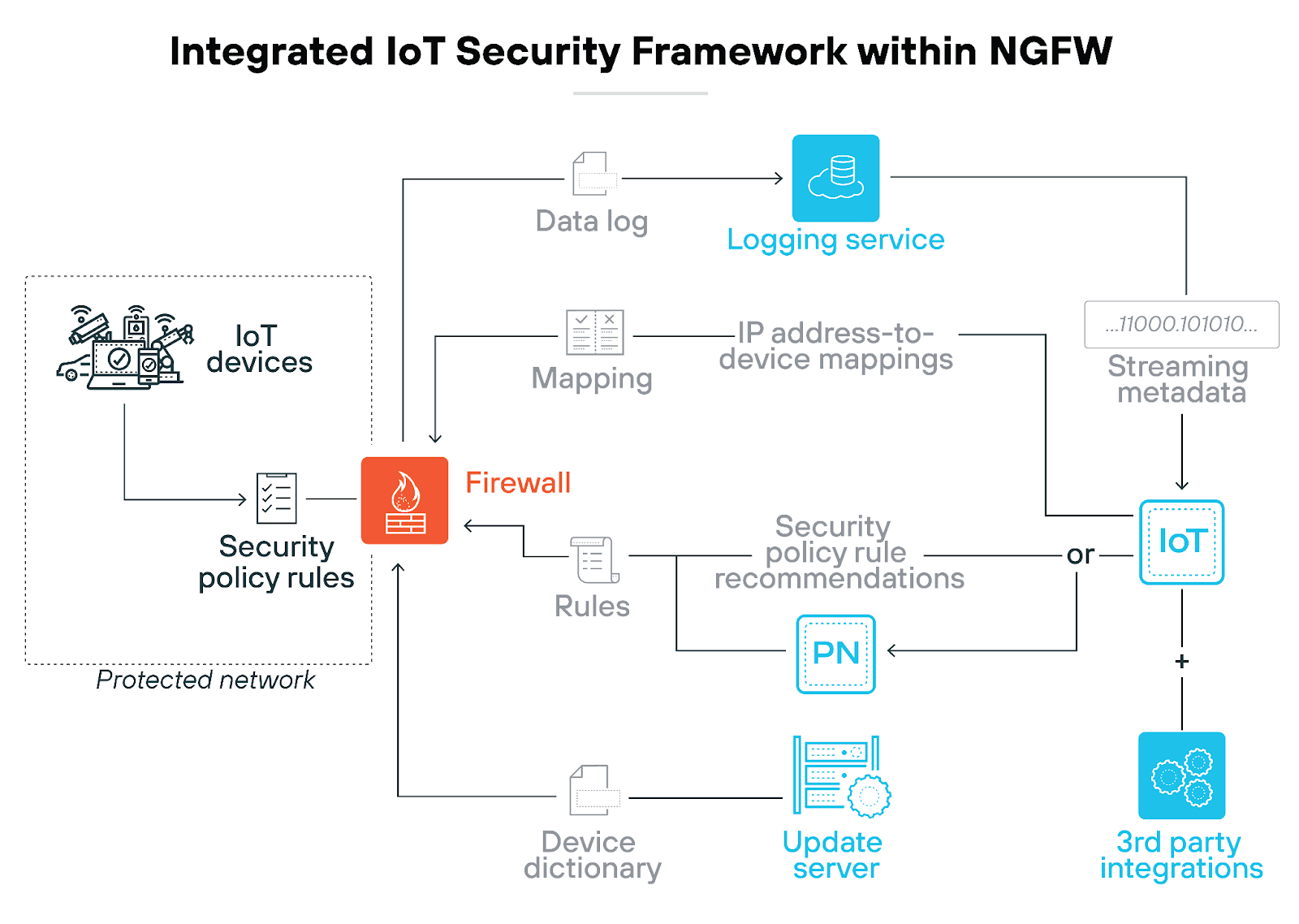
NGFWs equipped with IoT security capabilities use advanced techniques to monitor and manage the traffic from these devices. This includes identifying device types, tracking behavior patterns, and ensuring that all communications adhere to established security policies.
This monitoring helps detect and prevent anomalous behavior that could indicate a security threat, such as unauthorized access or data exfiltration attempts. By implementing predefined security rules, NGFWs can automatically block suspicious activities, providing real-time threat prevention.
Further reading: What Is IoT Security?
Next-generation CASB
A next-generation cloud access security broker (CASB) is an advanced NGFW feature designed to provide robust security across various cloud applications. This functionality is especially important because businesses are increasingly relying on SaaS applications that reside outside traditional security controls.
What exactly does a next-generation CASB do?
It acts as a gatekeeper between users and cloud services, monitoring all data traffic and enforcing security policies. Which prevents unauthorized access and data breaches (while ensuring compliance with internal policies and external regulations).
The CASB integrates seamlessly into the firewall to extend security measures beyond traditional network perimeters, directly into cloud environments.
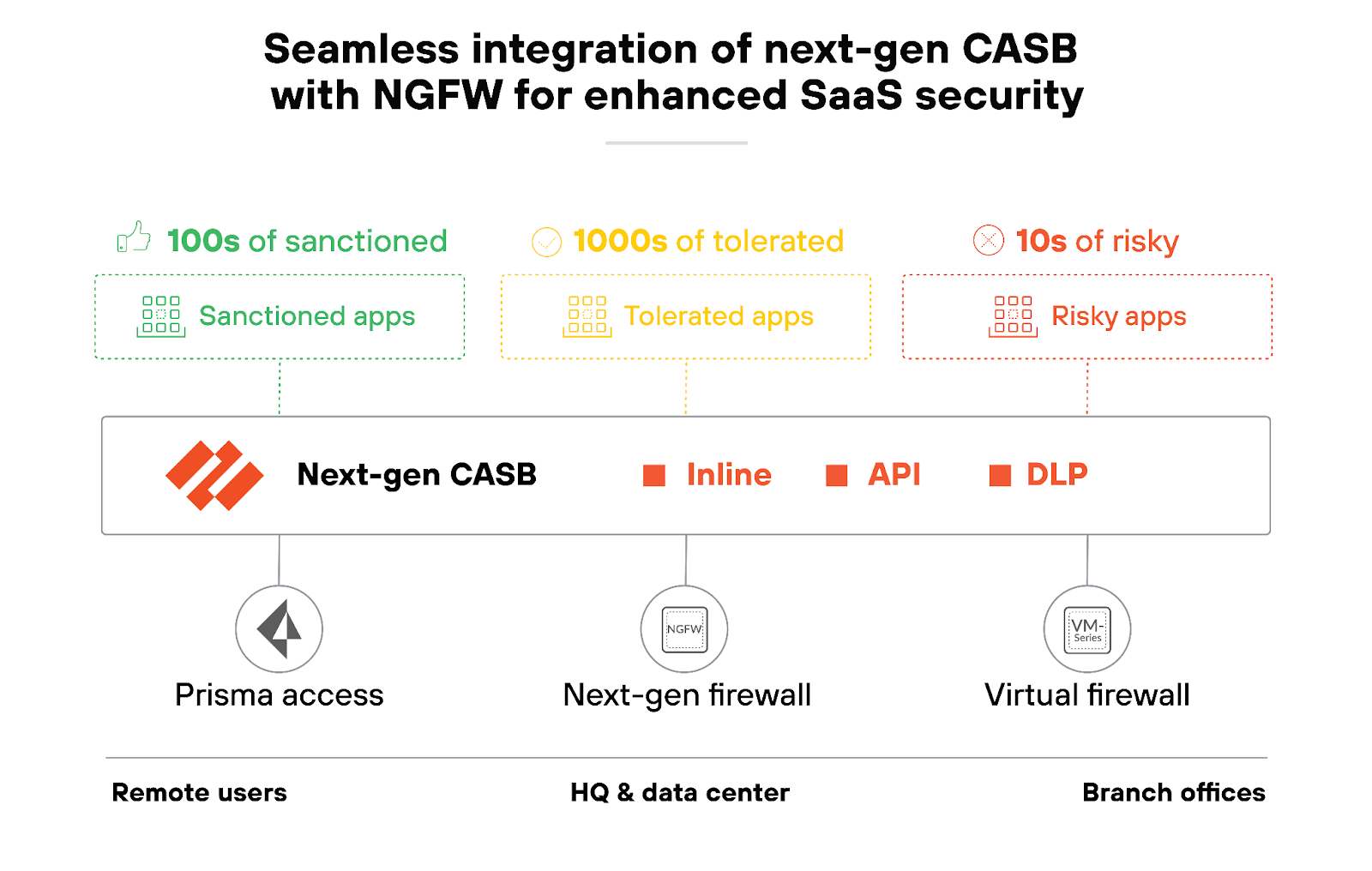
The CASB continuously evaluates the risk levels of cloud services, providing real-time security postures and visibility across all cloud platforms.
This matters because organizations continue to adopt more cloud-based tools. And that means that the risk of data leaks and security breaches increases.
A next-generation CASB addresses these challenges by offering granular control over data access and usage across all cloud services. Including sanctioned and unsanctioned applications. So organizations can embrace the benefits of cloud computing and maintain stringent security controls.