SD-WAN vs. SASE: Where One Ends and the Other Begins
The difference between SD-WAN and SASE is that SD-WAN is a networking technology that optimizes wide-area connectivity, while SASE is a framework that converges SD-WAN with cloud-delivered security.
SD-WAN focuses on routing traffic across multiple links to improve performance and efficiency. SASE extends this by unifying connectivity with security functions for distributed users and applications.
What is SD-WAN?
Software-defined wide area networking, or SD-WAN, is a networking technology that changes how organizations connect their branch offices, data centers, and cloud services. Instead of depending on a single private line such as MPLS, it can use multiple transport types at once. That includes broadband internet, LTE, and other available connections.
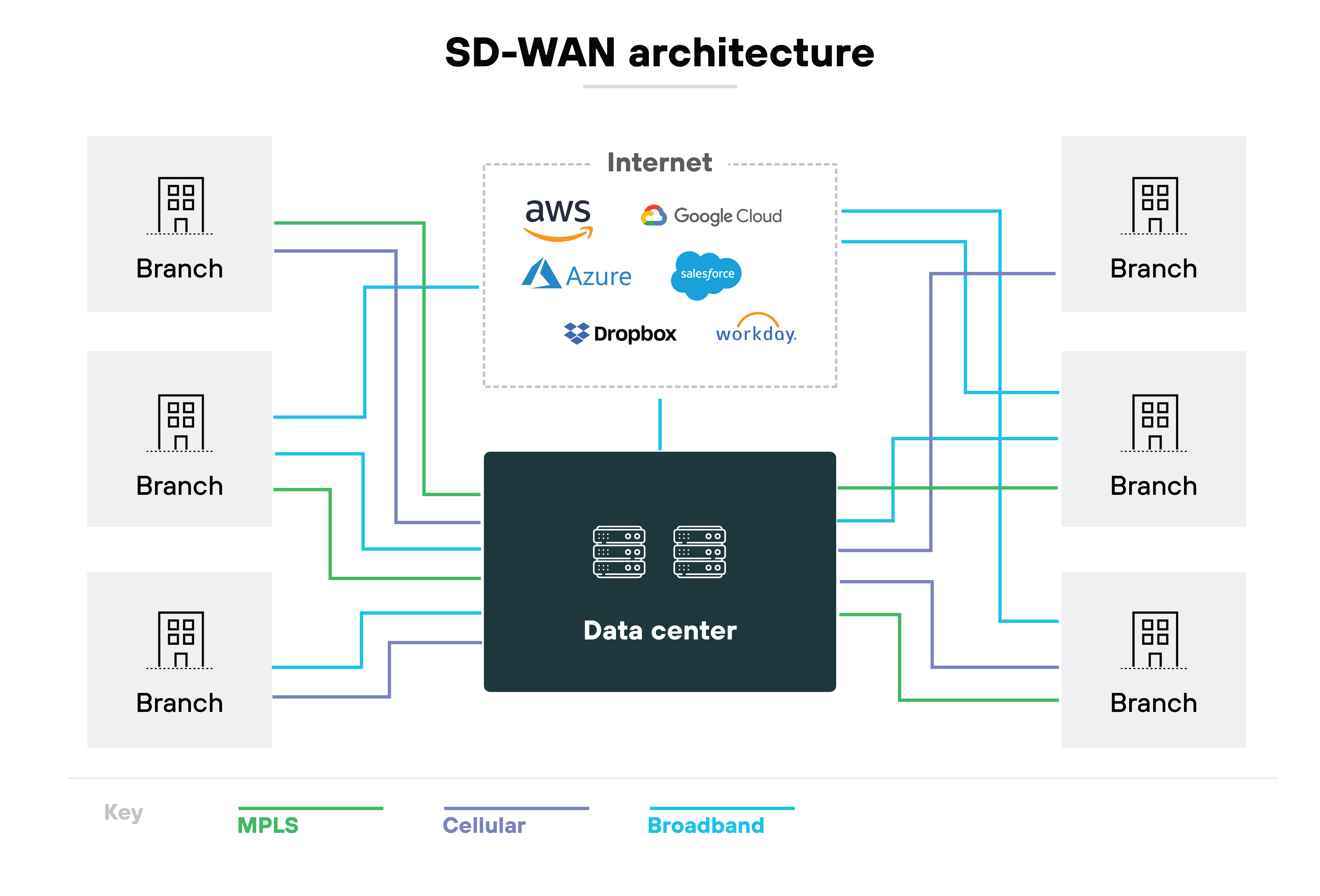
The purpose is simple. Improve the performance, efficiency, and flexibility of the wide area network.
Here's why it matters:
Traditional WAN architectures were rigid and tied to expensive private circuits.
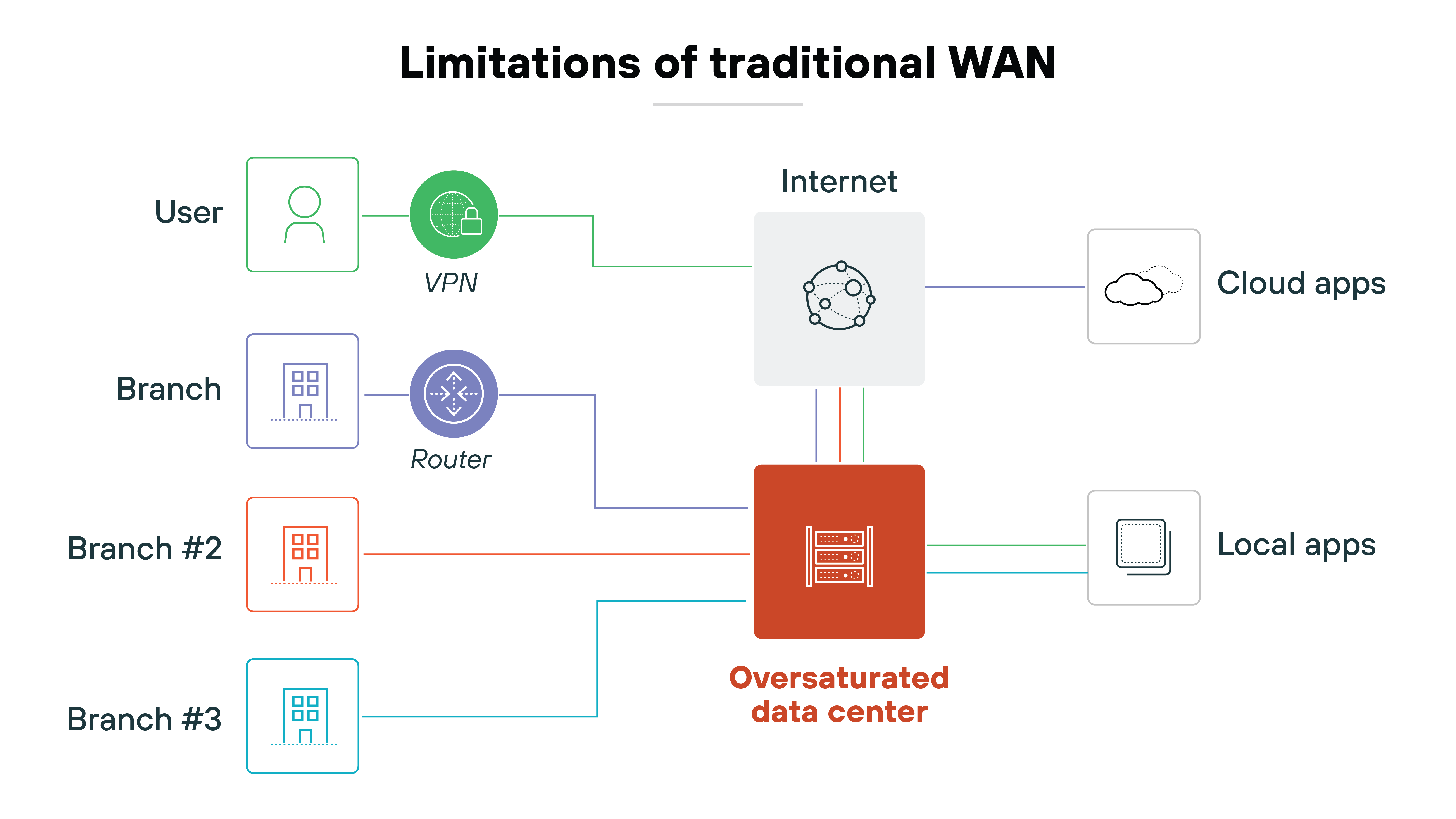
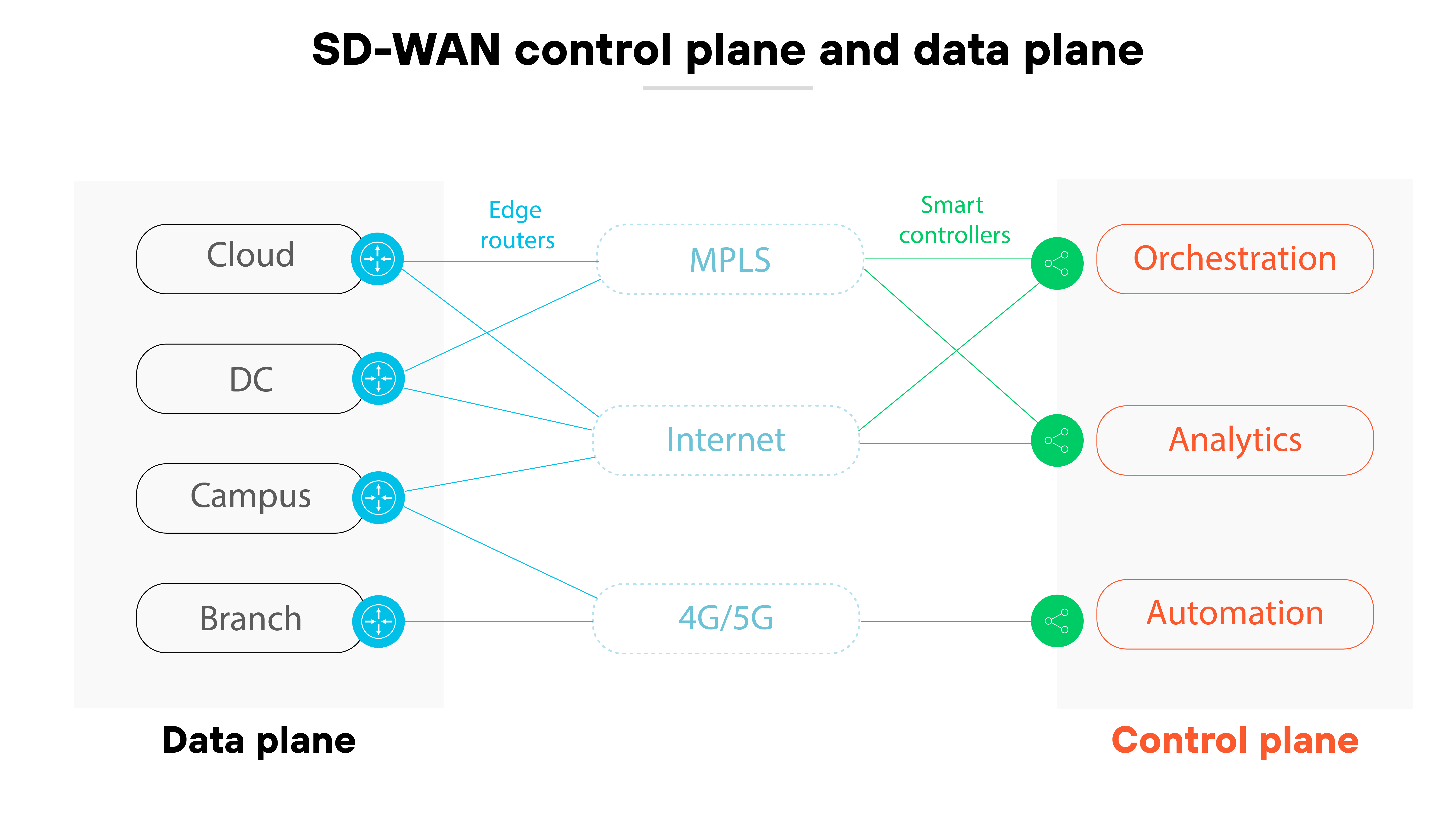
But SD-WAN separates the control and data planes. And that allows policies to steer traffic across the best available path in real time. Path selection is based on application requirements and business rules. Not just static routing.
In practice, that means the network can automatically shift traffic if a link becomes congested or fails. Applications like voice or video can be prioritized to maintain quality, while less sensitive traffic can be sent over cheaper links.
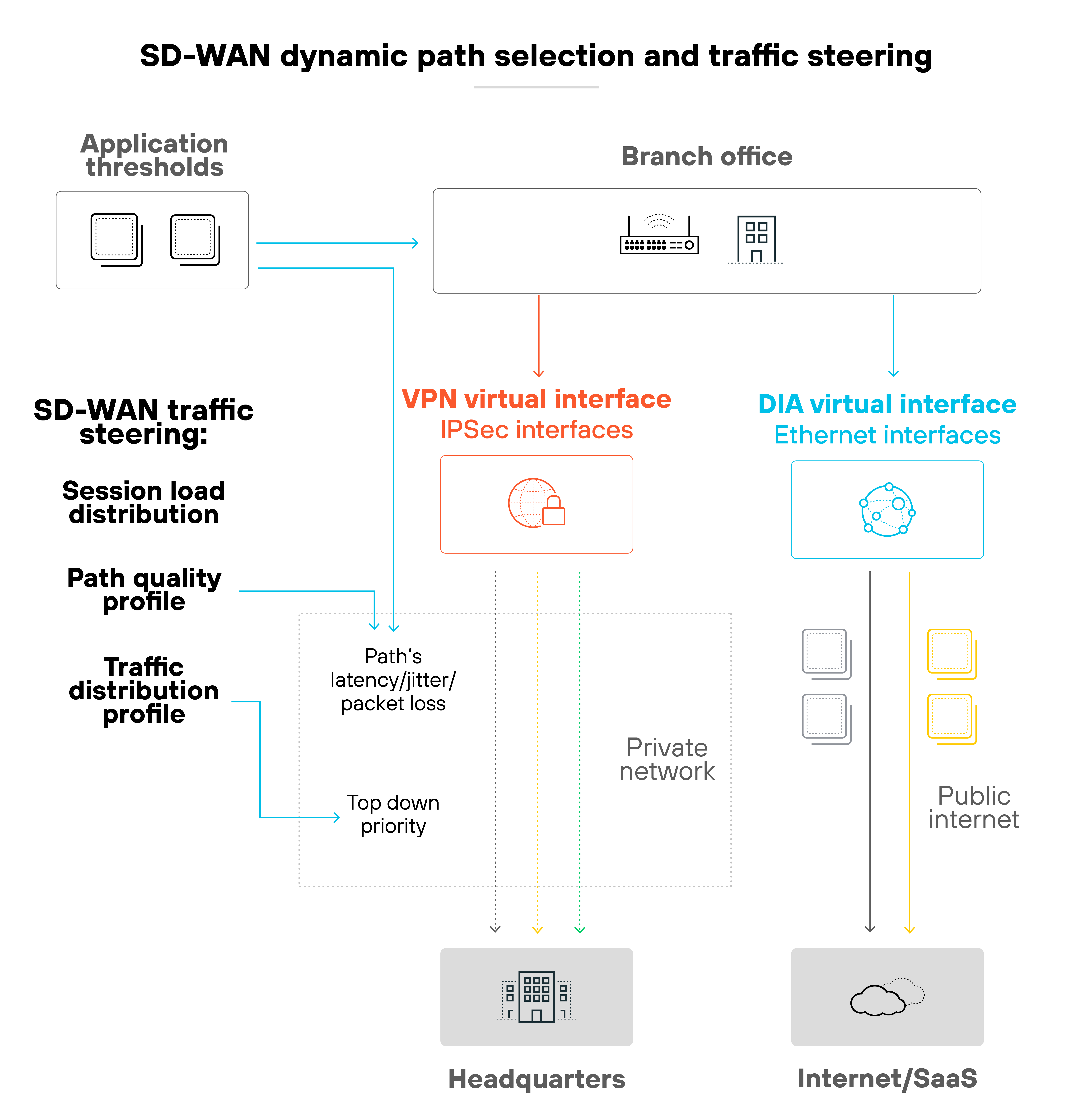
Essentially, SD-WAN is about optimizing WAN connectivity. It replaces the limitations of legacy routing with centralized orchestration, dynamic path selection, and transport independence. Which means the network becomes more resilient, adaptive, and cost-efficient without changing how users or applications interact with it.
- What Is SD-WAN Architecture? [Components, Types, Importance]
- Types of SD-WAN Deployment Models: A Complete Guide
What is SASE?
Secure access service edge, or SASE, is a framework that merges networking and security into a single cloud-delivered model. Instead of relying on separate hardware appliances, it provides both connectivity and protection through distributed points of presence.
The goal is straightforward. Secure and connect users, applications, and data–no matter where they're located.
Here's how it works:
SASE brings together networking and security into a single framework.
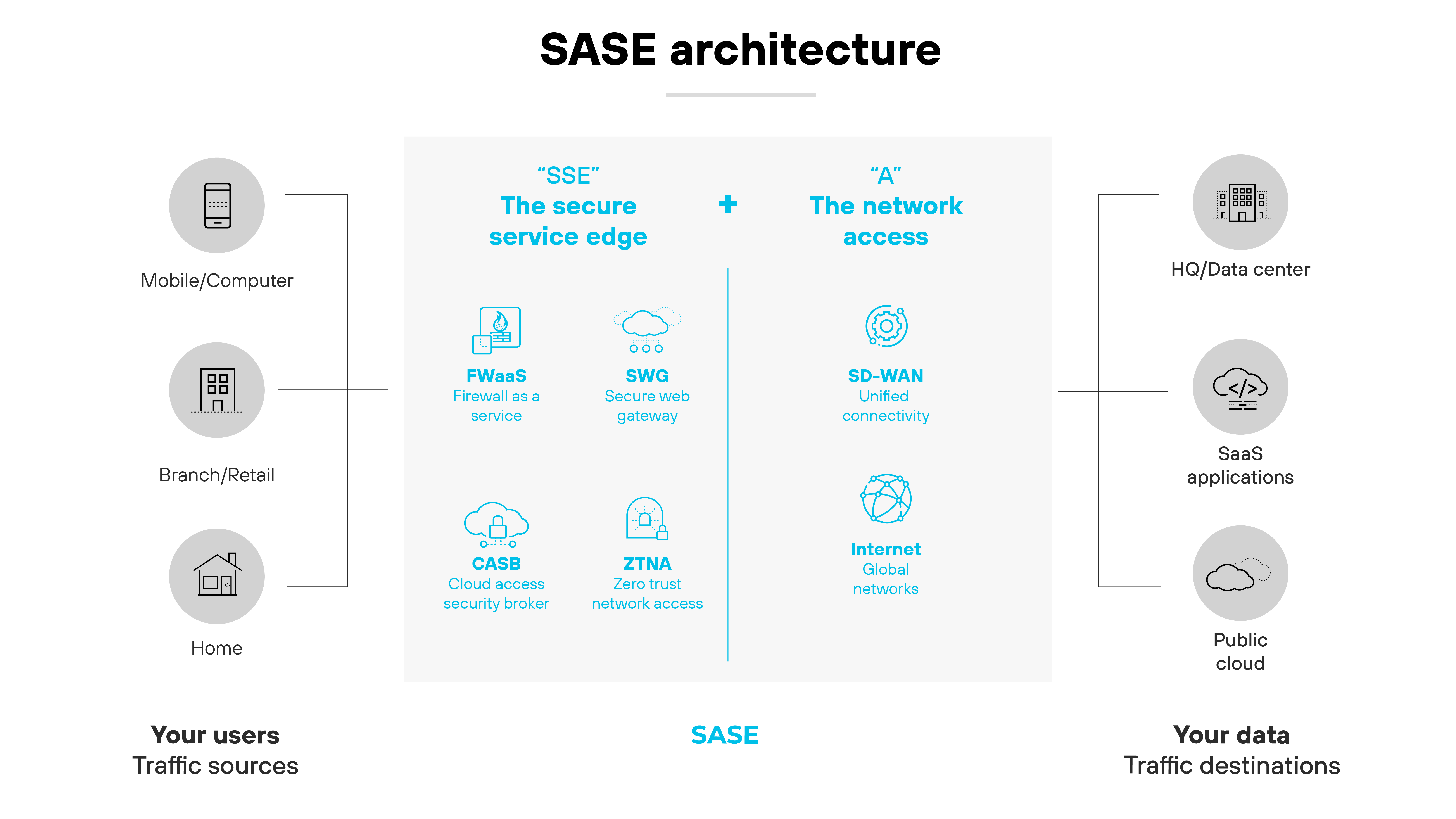
SD-WAN is the networking foundation, which–as explained–manages connectivity across different links and locations. Security functions such as firewall as a service (FWaaS), secure web gateway (SWG), cloud access security broker (CASB), and zero trust network access (ZTNA) are integrated alongside it.
Together, these capabilities let organizations apply consistent policies and enforce access across cloud, branch, and remote environments.
It's important to note that SASE isn't just a collection of tools. It's an actual architectural approach that shifts networking and security to the cloud. And that shift is what allows organizations to scale, reduce complexity, and deliver a unified experience to users working from anywhere.
In short: SASE equals SD-WAN plus a cloud-based security stack. It's the model enterprises are adopting to replace fragmented legacy systems with a converged way to connect and protect.
How are SD-WAN and SASE related?
SD-WAN and SASE aren't separate technologies competing with one another. They're connected. And that's because SD-WAN is one of the essential components inside a SASE framework, as discussed.
Let's break this down.
Again, SD-WAN was designed to solve wide area networking challenges. So it gave organizations the ability to move away from rigid private circuits and route traffic dynamically across multiple connections. And that definitely made networks more flexible and cost-efficient.
But what it didn't do was solve the security problem.
For example(s):
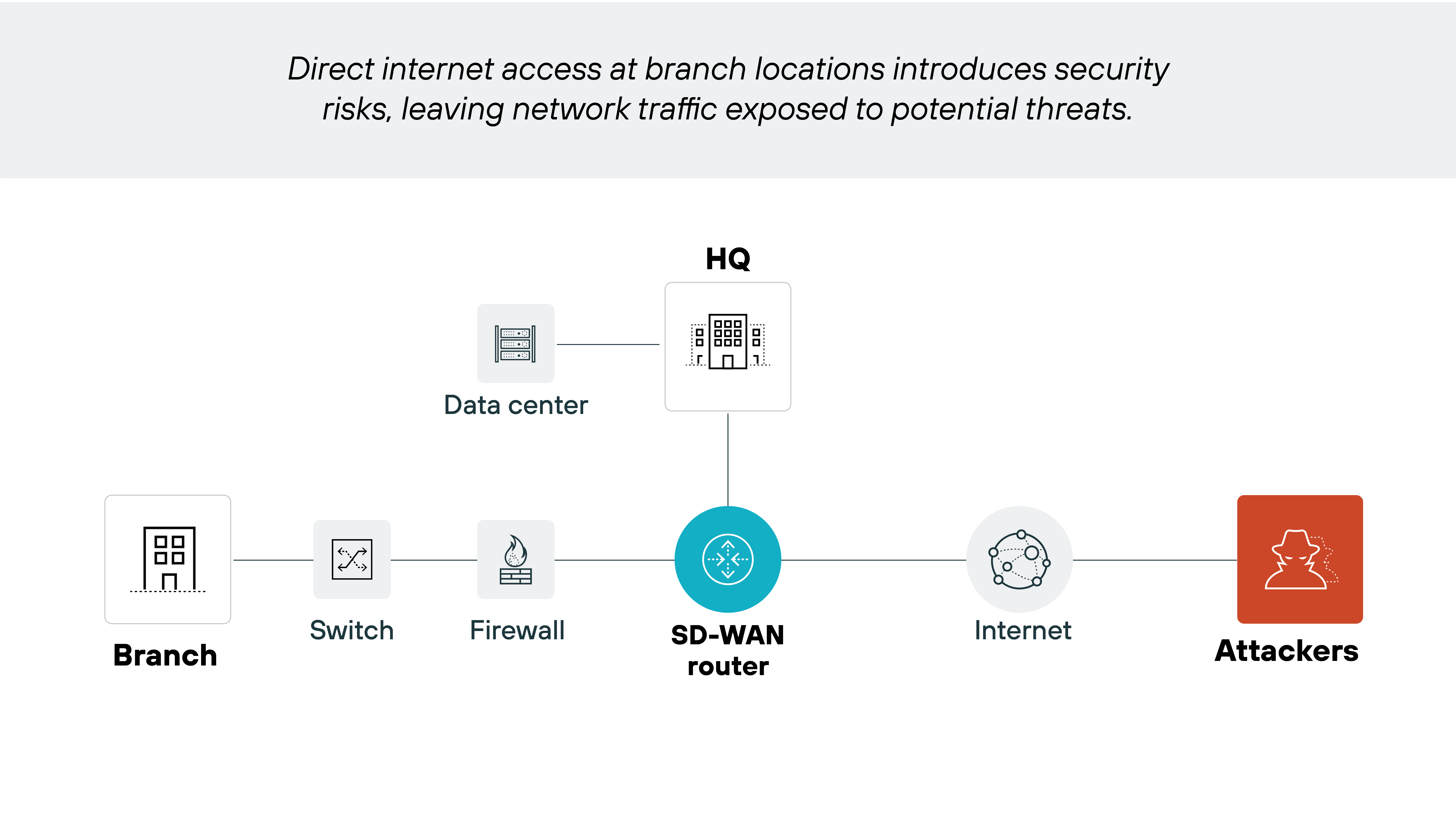
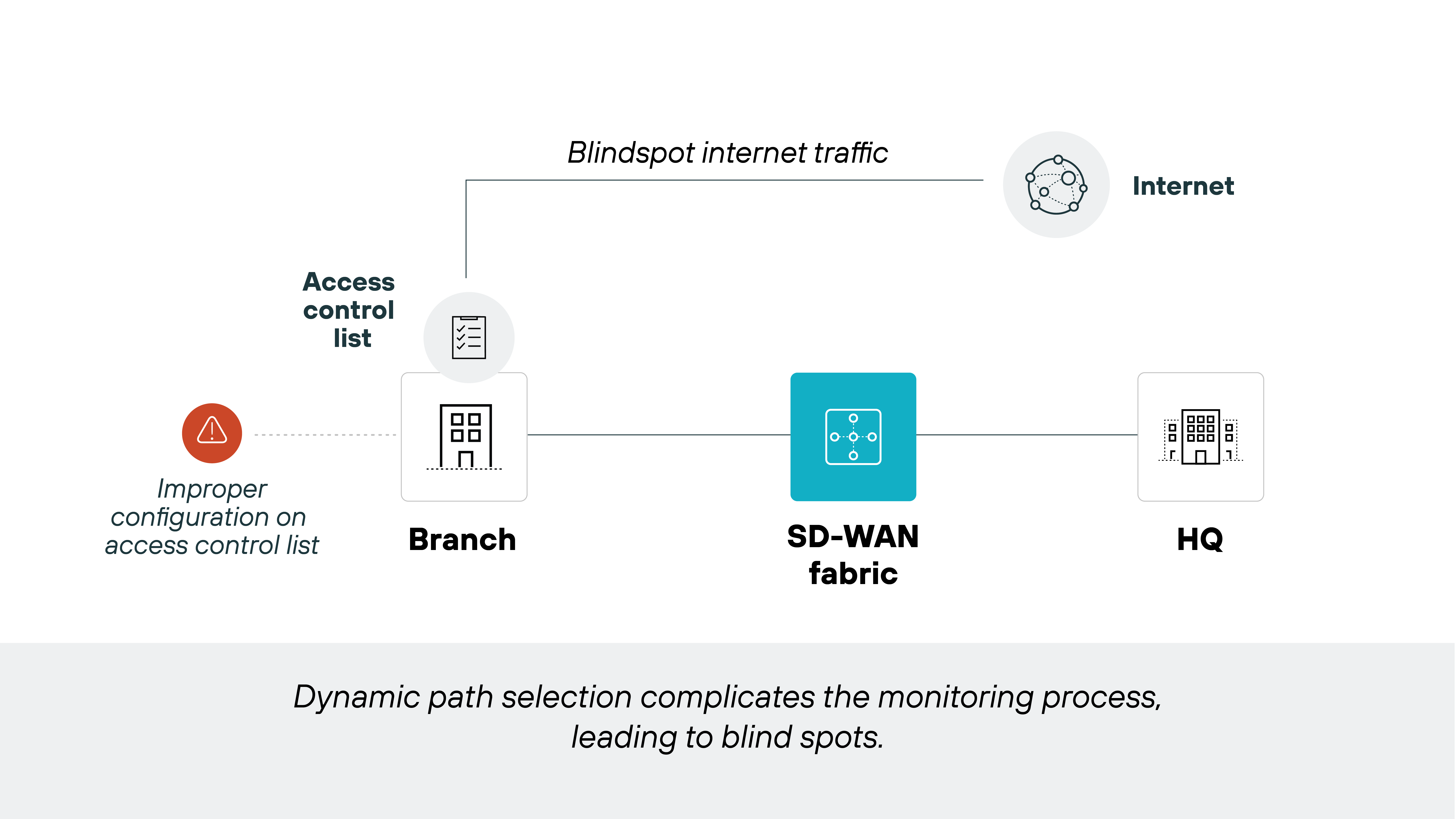
So traffic still had to be secured by separate tools and appliances.
And that's where SASE came in. It built on SD-WAN's networking foundation and added the missing security services–all the functions we covered previously (SWG, CASB, FWaaS, and ZTNA). They all converge with SD-WAN under a single cloud-delivered model.
Think of it as an evolution path:
- Legacy WAN was built on MPLS and fixed architectures.
- SD-WAN introduced transport independence and centralized control.
- SASE extends that progress by converging networking and security together in the cloud.
Remember:
SASE still depends on SD-WAN for connectivity. The networking layer provides the basis for applying global security policies and ensuring reliable access. Without SD-WAN's traffic steering and link optimization, SASE wouldn't be able to deliver consistent performance for distributed users and applications.
The bottom line is this. SD-WAN is the transport fabric. SASE is the broader framework that uses that fabric to connect and secure everything everywhere. So one is embedded inside the other.
- Top 7 SD-WAN Challenges: SD-WAN Risks, Issues, & Solutions
- What Is SD-WAN Security? | SD-WAN Security Considerations
Does SASE replace SD-WAN?
It's a common misconception that adopting SASE means getting rid of SD-WAN. But that isn't the case.
This view often comes from how SASE is described as the “next evolution” of SD-WAN, which can make it sound like a direct replacement. Confusion also comes from procurement discussions, where buyers are often encouraged to consider SASE platforms instead of separate SD-WAN deployments.
So what does change?
The scope.
SD-WAN focuses on networking. As mentioned, it makes the WAN more efficient. But SASE takes that same networking base and adds the security functions organizations need today.
So SASE doesn't replace SD-WAN. It extends it.
Architecturally, this is how SASE integrates SD-WAN alongside its security layers:
Organizations still deploy SD-WAN. But it comes as part of a larger cloud-delivered framework that unifies networking and security in one architecture.
To put it simply, SASE builds on SD-WAN to give organizations integrated security and connectivity in the cloud era.
When should you use SD-WAN vs. SASE?
The choice between SD-WAN and SASE depends on your environment and priorities. It's not really a matter of one versus the other. It's about what your organization needs now, and what it will need later.
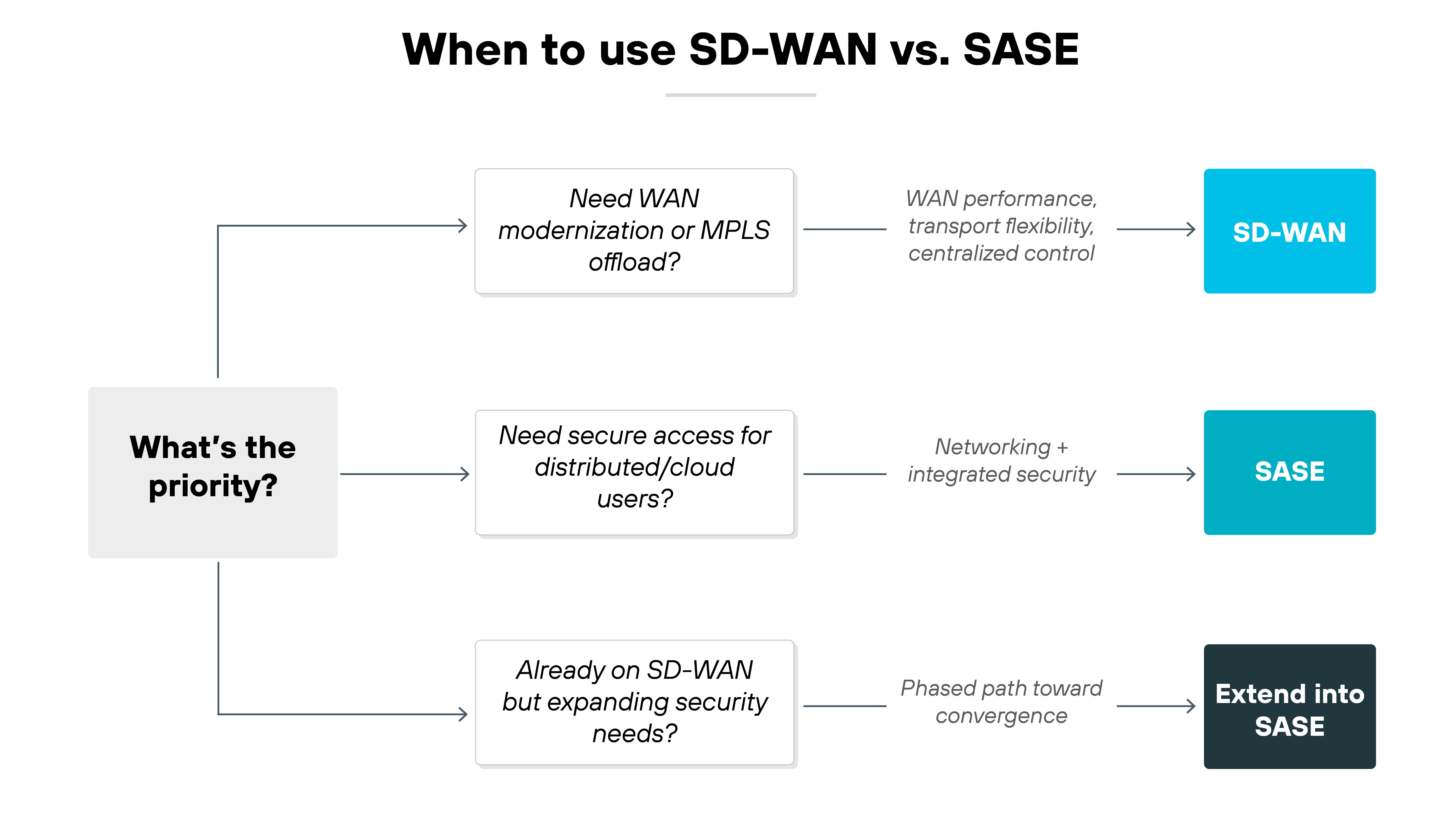
Start with SD-WAN when the main challenge is modernizing the wide area network.
For example, if you're trying to offload expensive MPLS connections or improve performance between branch offices and data centers. SD-WAN can deliver better routing, transport flexibility, and centralized control without requiring a major architectural change.
On the other hand, SASE makes more sense when networking and security need to come together.
Distributed workforces, cloud adoption, and a push toward Zero Trust are the drivers. Organizations that want consistent policy enforcement across users, applications, and devices will find that SASE's cloud-delivered model addresses gaps that SD-WAN alone cannot.
And don't forget: this isn't an all-or-nothing decision.
Many organizations deploy SD-WAN first, then extend into SASE as requirements evolve. Hardware refresh cycles, existing vendor contracts, and team structures often dictate a phased path. And that means SD-WAN may be a starting point, while SASE is the eventual destination.
To sum up: use SD-WAN when the priority is WAN performance and cost optimization. Use SASE when the priority is securing access everywhere. And recognize that most enterprises will move through both stages on the way to a fully converged model.
What are the main differences between SD-WAN and SASE?
Let's get into the nuts and bolts of how SD-WAN and SASE diverge in terms of scope.
Both improve connectivity, but they were designed to solve different problems. The table below breaks down how:
| Comparison: SD-WAN vs. SASE |
|---|
| Dimension | SD-WAN | SASE |
|---|---|---|
| Core focus | Application-aware WAN connectivity and optimization | Unified framework for secure connectivity everywhere |
| Key components | SD-WAN edge devices, controllers, policies, and overlays | SD-WAN + security services (FWaaS, SWG, CASB, ZTNA, etc.) |
| Security coverage | Limited to encryption and basic segmentation | Broad, integrated security stack enforcing Zero Trust |
| Deployment model | Hardware or virtual appliances at sites, managed centrally | Cloud-delivered model using distributed points of presence |
| Primary use cases | MPLS offload, branch-to-branch and branch-to-cloud optimization | Secure access for hybrid work, cloud adoption, and global policy enforcement |
| User scope | Branch offices and data centers | Users, devices, and applications anywhere |
It can't be said enough: the two aren't competing choices. SD-WAN provides the transport layer that SASE builds on. And that makes it the logical starting point for many organizations– and a permanent part of any SASE deployment.