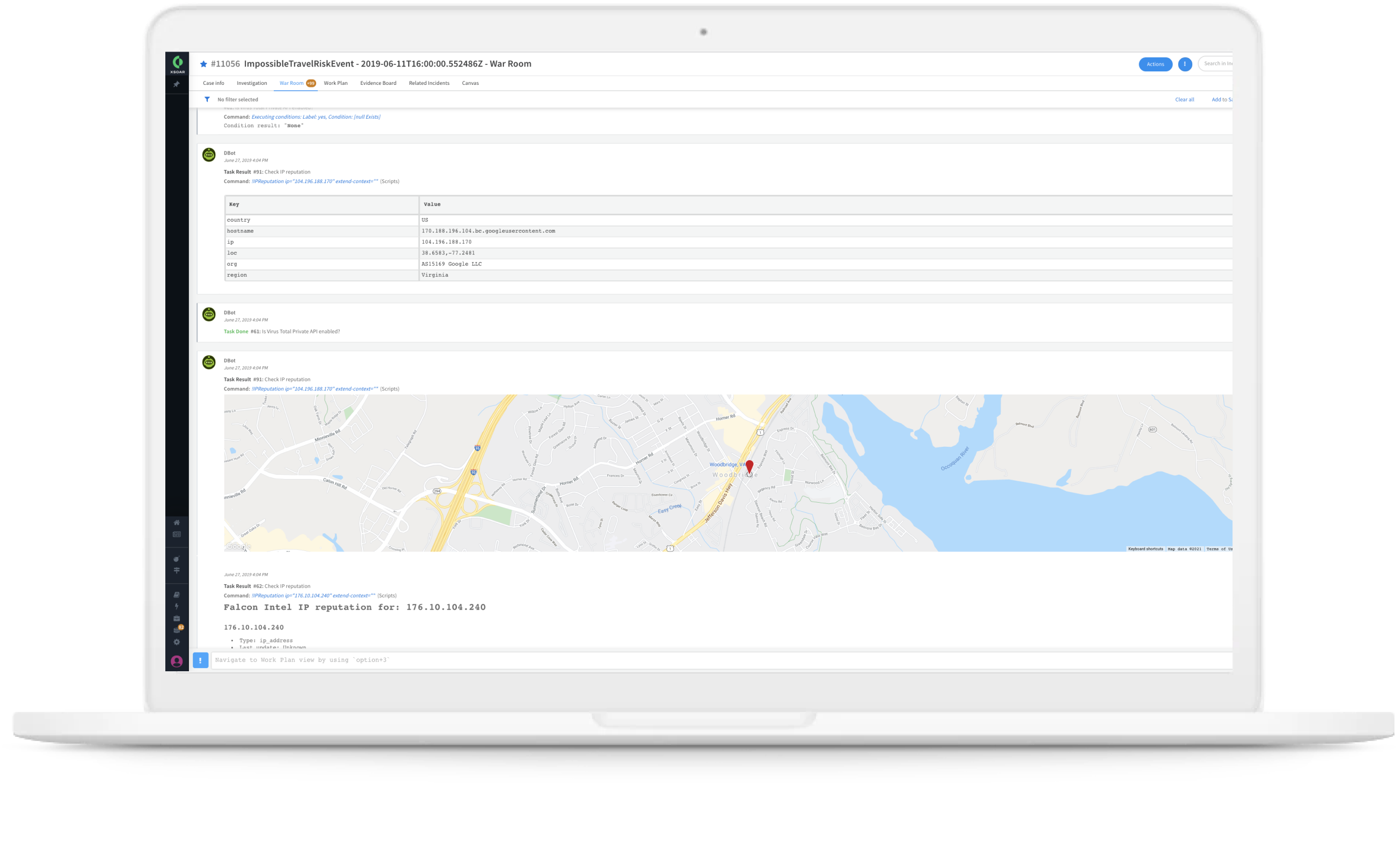
A war room for every incident
Each incident is associated with a war room where analysts can do investigations and collaborate in real time. Significant incident artifacts can also be easily tagged as evidence, and all actions performed by playbooks or analysts are auto-documented.
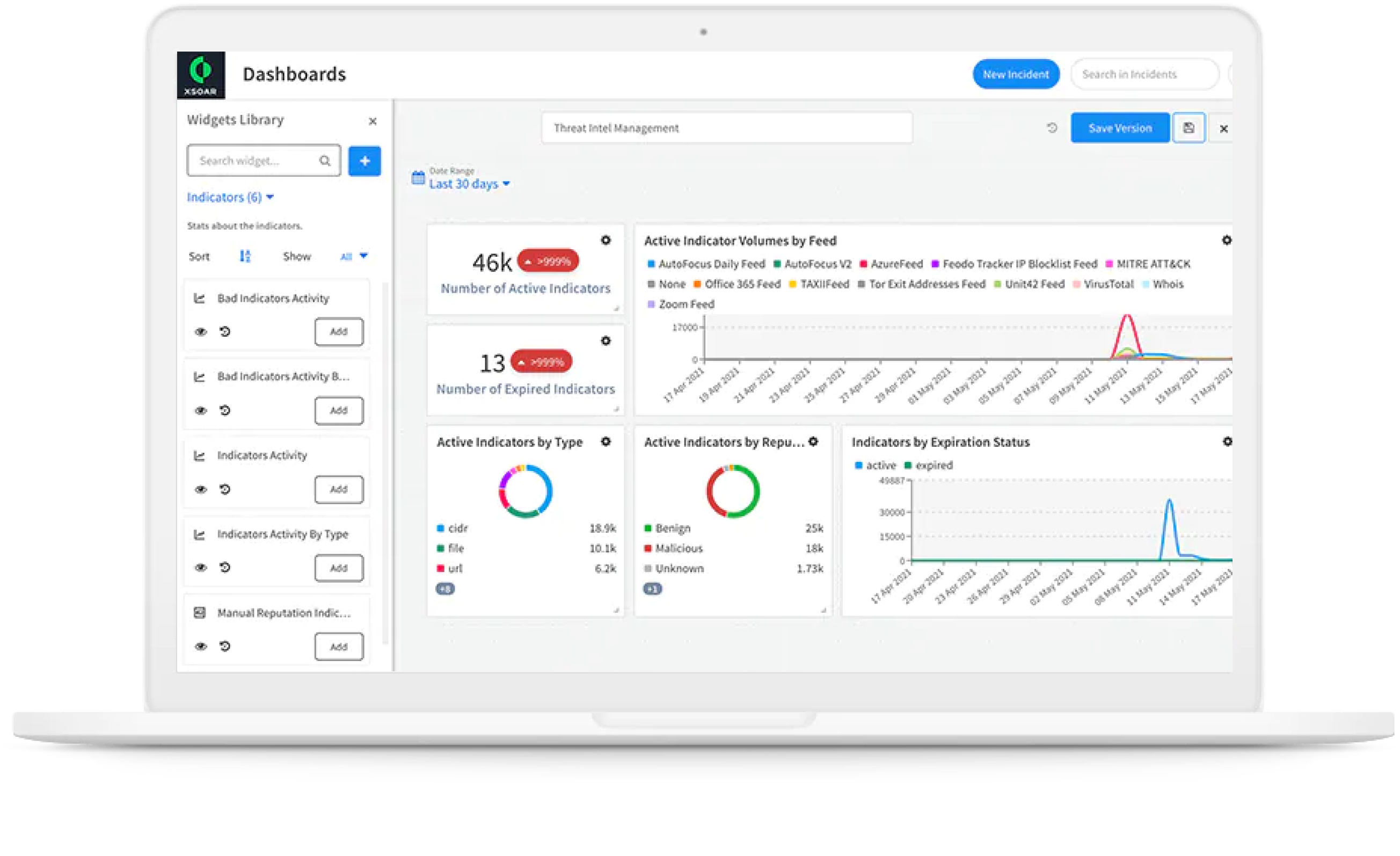
Incident-specific layouts
Get incident views and flows specific to incident type, so all relevant data is at your fingertips. Create custom tabs and layouts for any incident type with full role-based access control.
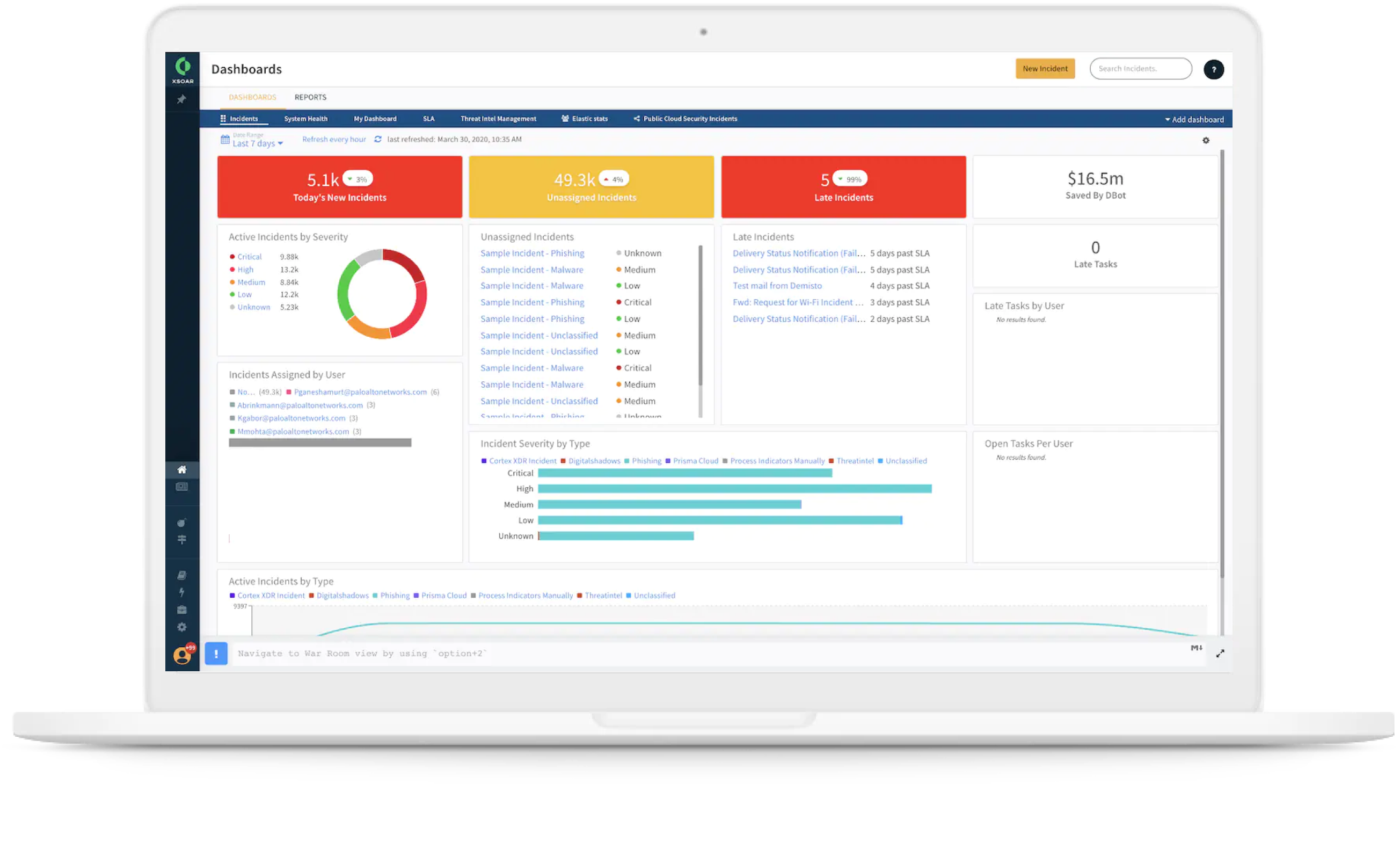
Centralized ticket repository
Manage all your security incidents from one location. Full ticket mirroring with tools like ServiceNow, Jira and Slack allow you to automate ticketing tasks and manage your tickets from one location.